Foundations Of MITRE ATT and CK v13
Introduction
The non-profit group MITRE works in several government-funded areas, such as homeland security, aviation, civil systems, defense, intelligence, and healthcare. MITRE is renowned for establishing adaptable frameworks and shared vocabulary that bring industries together.
This blog focuses on the ATT&CK Framework, managed by MITRE Engenuity. MITRE Engenuity drives innovation and collaboration in cybersecurity by bringing together experts, researchers, and organizations from both the public and private sectors. It fosters a trusted environment for knowledge sharing and the development of solutions to emerging cybersecurity challenges, continuously improving the ATT&CK Framework. In addition to the ATT&CK Framework, MITRE Engenuity works on initiatives like the Center for Threat-Informed Defense (CTID) and the Cybersecurity Testing and Evaluation program. These initiatives aim to enhance cybersecurity through practical solutions and validation of security tools.
ATT&CK Evaluations
An essential part of the larger ATT&CK project, ATT&CK evaluations evaluate how well different cybersecurity systems identify and counteract actual threats.
Through the simulation of known adversary tactics, methods, and procedures (TTPs), these assessments offer security vendors and practitioners a rare chance to gain a deeper understanding of the advantages and disadvantages of their products and services.
1.1 Threat-Informed Defense
Three components make up a Threat Informed Defense, a proactive approach to cyber security that gives your security team an evolving feedback loop:
- Cyber threat intelligence analysis
- Defensive engagement of the threat
- Focused sharing and collaboration
Cyber Threat Intelligence Analysis
A threat-informed defense first begins with being threat-informed and being informed requires threat intelligence. With intelligence, you are able to understand who is likely to attack you and how they are likely to do it. This information gives you the basis for your defenses.
Threat Intelligence Analysis is taking existing intelligence data like TTPs, malware hashes, or domain names, and applying human intelligence to harden cyber defenses. This improves ways to anticipate, prevent, detect, and respond to cyber-attacks.
MITRE CRITS
CRITs is a free, open-source tool for analysts and security professionals on threat defense. Developed in 2010, its main goal is to offer the security community an adaptable and open platform for analyzing and collaborating on threat data.
Defensive Engagement of the Threat
Using the knowledge you’ve gained from intelligence analysis, defensive engagement of the threat enables you to search for signs of an impending, ongoing, or successful cyberattack. The behavioral models found during intelligence analysis are used by Breach and Attack Simulation (BAS) tools, which enable you to automate testing and reporting on how certain behavior patterns appear in your organization.
2. The ATT&CK Framework
The MITRE ATT&CK framework is a widely used and important resource in the field of cybersecurity. It provides a comprehensive understanding of the tactics, techniques, and procedures used by cyber adversaries, which enables organizations to better identify, detect, and respond to cyber threats. As you’ll remember, threat intelligence and data-based decisions are a major part of a threat-informed defense. Understanding how your adversaries operate is incredibly valuable in defending your enterprise.
The framework is based on real-world observations of actual attacks, which means that it is constantly updated with new information and reflects the latest threat landscape. Additionally, The ATT&CK framework covers a wide range of threat actors, platforms, and use cases, and it can be used for not only detection and defense but also for planning and prioritizing security investments, measuring the effectiveness of security controls, and communicating with stakeholders. The ATT&CK framework has a community of researchers, practitioners, and enthusiasts who contribute to its development and improvement.
MITRE allows for contribution to the ATT&CK Framework through the submission of:
- New techniques and sub-techniques
- New techniques and sub-techniques for macOS, Linux, cloud, and ICS
- Threat Intelligence
- Data sources such as endpoint or network log data for techniques used in incidents
- Your use cases
2.1 ATT&CK Matrices
The ATT&CK framework is more than the single matrix you are used to seeing. There are, 3 matrices available to represent the ATT&CK Framework in different contexts. Those matrices are:
- The Enterprise Matrix
- The Mobile Matrix
- The ICS Matrix
Enterprise Matrix
The Enterprise Matrix is comprised of tactics and techniques that effect the following platforms:
- Windows
- macOS
- Linux
- PRE
- Azure AD
- Office 365
- Google Workspace
- SaaS
- IaaS
- Network
- Containers
As you can see, there are a wide variety of local host-based platforms, cloud-based platforms, network threats, and containers represented in this matrix. The Enterprise Matrix is most likely the matrix you are familiar with because it is so vast, yet detailed. For those reasons, it is the matrix we will reference throughout this class, unless stated otherwise.
Mobile Matrix
The Mobile Matrix covers techniques involving device access and network-based effects that can be used by adversaries without device access. Both iOS and Android operating systems are covered in this matrix.
The mobile matrix consists of 12 tactics:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
Within the Matrix you will find techniques that can apply both to the enterprise or mobile platforms. You will also find techniques that are specifically used on mobile platforms. One such technique is Access Notifications.
The description of Access Notifications reads: “Adversaries may collect data within notifications sent by the operating system or other applications. Notifications may contain sensitive data such as one-time authentication codes sent over SMS, email, or other mediums. In the case of Credential Access, adversaries may attempt to intercept one-time code sent to the device. Adversaries can also dismiss notifications to prevent the user from noticing that the notification has arrived and can trigger action buttons contained within notifications.”
ICS Matrix
The ICS Matrix covers tactics and techniques that apply to industrial control systems. Like the Mobile Matrix, there are 12 tactics. You will notice, however, that not all of those tactics are the same. The 12 tactics in the ICS Matrix include Initial Access:
- Execution
- Persistence
- Privilege Escalation
- Evasion
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Inhibit Response Function
- Impair Process Control
- Impact
You might have observed that certain tactics in the ICS Matrix are exclusive to it. For instance, the
Inhibit Response Functions include Alarm Suppression, Block Command Messages, and Manipulating I/O Image as its techniques. Another tactic is the Impair Process Control Tactic, which encompasses Brute Force I/O and Spoof Reporting Messages as techniques.
The Inhibit Response Function refers to the methods employed by cybercriminals to hamper the protective measures implemented for processes and products. On the other hand, the Impair Process Control Tactic refers to the ways in which attackers can interfere with control logic and lead to adverse impacts on the processes being managed in the target environment.
2.2 What are TTPs?
TTPs is known as Tactics, techniques, and procedures are key concepts in the ATT&CK framework.
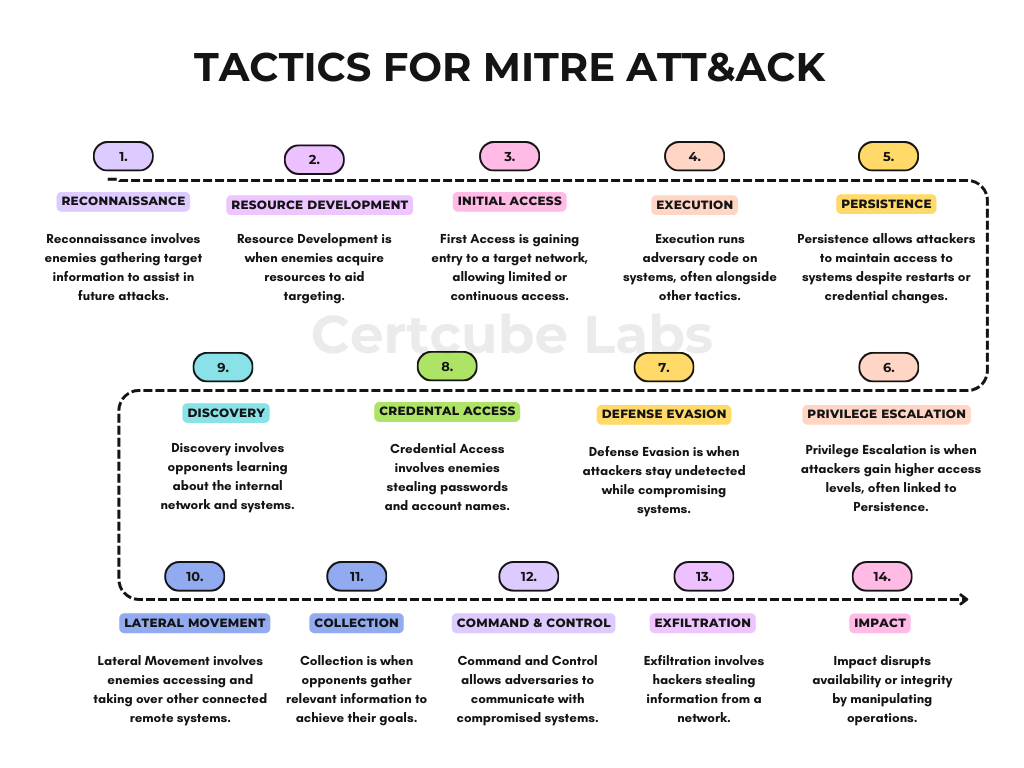
Tactics:
All of the strategies are divided into 14 tactics by the enterprise matrix, and each tactic has a distinct function in the adversary’s lifecycle.
The first approach, which goes from left to right, is reconnaissance, in which enemies proactively or inadvertently get data on a possible target, such as specifics regarding the victim organization, individuals, or infrastructure. This data can help with other stages of the adversary lifecycle and enable targeting.
The second strategy is called “Resource Development,” in which enemies build, buy, or steal resources—like accounts, infrastructure, or capabilities—that can be utilized to facilitate targeting.
First Access is the third strategy(Initial Access), which entails establishing a presence in the target network through a variety of entrance vectors. These footholds might be restricted in usage because passwords change, or they might permit continuous access.
Execution, the fourth approach, causes adversary-controlled code to run on a system that is either local or remote. To accomplish more ambitious objectives, this tactic is frequently combined with methods from other tactics.
The fifth strategy is persistence, in which attackers employ methods to maintain access to systems in the face of restarts, credential changes, and other disruptions that may prevent them from doing so.
The sixth strategy is called Privilege Escalation, in which attackers employ methods to obtain more privileged access to a system or network. This strategy frequently intersects with Persistence methods.
Defense Evasion is the seventh tactic, in which attackers employ strategies to stay under the radar while compromising systems.
The eighth strategy is known as Credential Access, wherein enemies pilfer credentials such as passwords and account names.
The ninth strategy is called “Discovery,” in which opponents employ methods to learn about the internal network and system.
The tenth strategy is called “lateral movement,” in which enemies employ methods to access and take over other remote systems connected to a network.
The eleventh strategy is called Collection, wherein opponents employ methods to obtain knowledge and the sources from which it is gathered that are pertinent to achieving their goals.
The twelfth tactic is Command and Control, these are techniques that adversaries use to communicate with systems under their control within the victim network.
Exfiltration is the thirteenth approach, in which a hacker employs methods to steal information from your network.
Finally, Impact, where adversaries use techniques to disrupt availability or compromise integrity by manipulating business and operations processes.
It’s important to note that these tactics are not mutually exclusive and often used in combination to achieve the adversary’s objectives.
Techniques & sub -techniques
The framework in its current iteration comprises 196 techniques that are distributed among the 14 tactics.
This technique has to do with gathering information about a victim’s network in order to plan and execute an attack.
There are six sub-techniques in this technique; let’s examine one to see how much more detailed it may be. We’ll use the Network Security Appliances sub-technique T1590.006 for this. By employing this method, adversaries are taking steps to determine which security appliances are present in your network. Adversaries can obtain this data by more passive methods like looking through online job advertisements for information on the technologies and abilities needed, or by using more direct collection techniques like Phishing for Information (T1598) or Active Scanning (T1595).
A new classification was added to the ATT&CK Framework in version 8.0. We refer to that classification as a “sub-technique.” Sub-techniques are a means of dissecting and characterizing the particular strategies employed by opponents to accomplish their objectives. The fact that each technique in the framework is composed of one or more sub-techniques allows for a more detailed knowledge of the techniques and their applications. The framework has 411 sub-techniques in version 13.
Procedures
The finer elements of an adversary’s acts within a sub-technique are essentially what procedures are. They detail the precise actions, equipment, or procedures an attacker uses to accomplish their goals. Security professionals can develop more specialized and potent protection tactics by looking closely at procedures, which will provide them a better grasp of how an assault proceeds.
Returning to our example of a spearphishing attachment, a procedure could specify the exact kind of attachment (a malicious PDF, for example), the targeted or spoof email accounts, the social engineering strategies used to fool the target, or the particular program or tool used to generate and distribute the spearphishing email.
Understanding procedures is crucial because they help organizations:
- Recognize trends and patterns in the actions of your adversaries to improve the accuracy of threat attribution.
- Create specialized security measures to thwart particular risks or methods of attack.
- Gain a deeper comprehension of the techniques used by attackers to bolster their threat intelligence skills.
- By understanding what to look for and how to react to certain techniques used by an attacker, organizations can improve their incident response systems.
2.3 Procedures vs. Sub-techniques
Procedures
Procedures are one of the most difficult concepts to learn. At first glance, they appear to be the same sub-technique. What separates procedures from one another? Remember that sub-techniques are a way of dissecting and describing the specific strategies used by opponents to achieve their goals. Spearphishing Attachment, the sub-technique we previously discussed, is still a pretty common tactic used by adversaries. Although it is more detailed than “Phishing,” it still doesn’t specify how to deliver an attachment in a phishing email.
Sub-techniques
To get initial access to the victim’s machine, the sub-technique involves sending a malicious attachment in conjunction with a targeted email (TA0001). Spearphishing via Service (T1566.003) and Spearphishing Link (T1566.002) are two more, similar sub-techniques of Phishing. Spearphishing is a type of social engineering that is sent electronically to a specific person, group, or sector. Using this method, the attackers attach a file to the email and wait for the recipient to open it in order to carry out their plan.
2.4 Data sources & mitigations
“Data sources represent the various subjects/topics of information that can be collected by sensors/logs,” reads the ATT&CK website. Data components, which identify particular attributes or values of a data source pertinent to identifying a particular ATT&CK technique or sub-technique, are also included in data sources. This implies that we should anticipate a list of methods that the sensors or logs on a data source can identify for each data source. Additionally, we should anticipate learning which matrix is being referred to as well as how to identify the data source technique. To have a better grasp of various data sources, let’s take a closer look at a few of them.
Active Directory (DS0026): We can obtain several data components related to detection information and ATT&CK procedures from the Active Directory data source. For instance, Steal or Forge Authentication Certificates affect the data component Active Directory Credential Request (T1649). This kind of activity would be found by keeping an eye on issued certificates for anomalous activity and AD CS certificate requests. Unexpected certificate enrollments and indications of certificate attribute abuse may be examples of this.
Command (DS0017): “A directive given to a computer program, acting as an interpreter of some kind, in order to perform a specific task” is the definition of the Command data source. Access Token Manipulation and Command Execution are related techniques (T1134). You might keep an eye on the commands and parameters being executed for token modification in order to spot this activity on this data source. For more in-depth detection details, visit the MITRE ATT&CK website’s Data Sources section.
Mitigations:
Mitigations are proactive steps you can take to ensure that a technique or sub-technique is not executed successfully. There are specific mitigations specified for each of the three matrices (Enterprise, Mobile, and ICS). We will concentrate on mitigations that relate to the Enterprise ATT&CK Matrix for the purposes of this training.
With every verified mitigation, you will receive the following details:
- A description of the mitigation
- Meta details about the mitigation such as ID, Version, Created Date, and Last Modified date.
- A listing of techniques that are addressed by the mitigation. Each listing consists of:o the matrix it is applied to under the Domain column,o the technique or sub-technique ID,o the technique or sub-technique name, ando a description of the use of the mitigation against the technique or sub-technique.
2.5 Threat Intelligence
Two essential components of threat intelligence are provided by the MITRE ATT&CK framework: the methods and instruments your adversaries employ to carry out their operations. When we refer to a software listing in ATT&CK, the ID provided will start with an S (rather than a T or TA), so you can know.
Groups are also identified by an ID that starts with a G.
Furthermore, there are Campaigns that combine elements of the software your opponents employ with their behavior.
Threat Groups: According to the ATT&CK structure, groups are collections of connected activities that make use of the same tools or software. The word “Group” is used by the MITRE ATT&CK team to refer to several designations for the activity cluster of an adversary. Techniques published in open sources are connected to groups, and the original references are given. Groups are also connected to campaigns and software that have been reported.
Campaigns: The MITRE ATT&CK team utilizes the term “campaign” to refer to any grouping of intrusion activity carried out over a predetermined length of time with shared targets and objectives for the purposes of the Campaigns page. The team will use the activity name as reported in public reporting unless the intrusion activity is unnamed and is cited using a special ATT&CK identification. The team tries its hardest to monitor overlapping names for specified campaigns; these are labeled as “Associated Campaigns” on each page since we think analysts will find these overlaps helpful. According to public reporting, campaign entries will also be linked to the ATT&CK Group and Software pages wherever feasible; unattributed activity will only mention “threat actors” in the method example.
3. Operationalizing ATT&CK
We should talk about the tools available to assist you in managing and utilizing the ATT&CK Framework so that you can use the intelligence inside your business, now that we have a better understanding of how the framework’s components interact to give you with intelligence.
3.1 Tools to Help You Operationalize ATT&CK
MITRE ATT&CK Navigator
A tool for exploring, annotating, and visualizing the ATT&CK matrix is the MITRE ATT&CK Navigator. It makes using and comprehending the matrix for cybersecurity reasons easier.
Key Features:
- Technique Highlighting: Apply filters to highlight techniques used by specific threat groups, helping organizations prioritize high-risk techniques.
- Customization: Add annotations or color-code techniques based on relevance or other criteria to create a tailored view.
- Layer Management: Create, import, and export custom “layers” of the matrix for collaborative threat analysis.
- Integration: Seamlessly share and analyze data across various cybersecurity systems.
Top ATT&CK Techniques Calculator
MITRE ATT&CK implementation can be difficult and expensive. The Top ATT&CK tactics tool offers a foundation for defense strategy by assisting defenders in ranking tactics according to critical criteria. Use the GitHub repository to access this tool.
Understanding the ATT&CK Workbench
Threat emulation methods, security tools, intelligence reports, and detection analytics are all over the cybersecurity scene nowadays. Even though MITRE ATT&CK mappings are incorporated into many security providers’ products, the sheer amount of data can be debilitating. The broad scope of the MITRE ATT&CK methodology can make it seem overwhelming to operationalize.
You’re always looking into alerts, separating out false positives from false negatives, and making sure your detection rules are working as they should as a member of the blue team. You need a method to keep track of new techniques you come across and utilize the ATT&CK framework to find coverage holes
Using known behaviors or TTPs from CTI teams or the ATT&CK framework, red team members simulate threats. It’s critical to demonstrate coverage against the MITRE ATT&CK paradigm, particularly for enterprises that prioritize continuous testing over infrequent red team operations
CTI teams must link new methods and references to threat groups or campaigns, regardless of whether they are using commercial, public, or in-house intelligence feeds. This makes it easier to monitor and evaluate security settings continuously.
3.2 MITRE DEFEND
According to the MITRE D3FEND website, “D3FEND is a knowledge base, but more specifically a knowledge graph, of cybersecurity countermeasure techniques. In the simplest sense, it is a catalog of defensive cybersecurity techniques and their relationships to offensive/adversary techniques.” D3FEND links the offensive model (ATT&CK) with the defensive model (D3FEND).
D3FEND Acronym:
- Detection
- Denial
- Disruption Framework Empowering Network Defense
D3FEND Matrix: The matrix allows cross-correlation of the ATT&CK Framework with defensive actions for detecting or disrupting attacker techniques. Tactics at the top vertical axis include:
- Model: Applies security engineering, vulnerability, threat, and risk analyses to digital systems.
- Harden: Increases the opportunity cost of computer network exploitation; generally conducted before a system is operational.
- Detect: Identifies adversary access to unauthorized activities on networks.
- Isolate: Creates barriers reducing adversaries’ opportunities for further access.
- Deceive: Entices potential attackers to a controlled environment.
- Evict: Removes adversaries from a network.
Tactics break down into techniques and sub-techniques for specific knowledge graphs. The matrix can be searched by ATT&CK Technique ID, D3FEND Technique ID, or Artifact
D3FEND artifacts: These comprehensive descriptions of defensive strategies and tactics include information on how they operate, how successful they are, and how they might be used to counter particular cyber threats. Examples and scenarios are provided by the categories of artifacts, which include network defense, endpoint defense, and data protection.
Example: Valid Accounts (T1078):
- Search T1078: Results in the Valid Accounts page with the “D3FEND Inferred Relationships” chart.
- Authentication Event Thresholding:
- Detects Valid Accounts (T1078)
- Analyzes Authentication
- Valid Accounts (T1078) uses User Account
- Produces Authentication and Authorization
Authentication Event Thresholding Page:
- Definition: Description of the control.
- How it works: Detailed explanation of the control’s functionality.
- Actions: Possible actions post-analysis.
- Example data sources: Useful data collection points.
- Considerations: Implementation factors.
- Digital Artifact Relationships: Impact on digital artifacts.
- Related ATT&CK Techniques: Related techniques via the ATT&CK Matrix.
- References: Sources and additional information.
Example Data:
Authentication Event Thresholding involves collecting authentication events to create a user profile and determining if new events deviate from this profile using thresholds. Actions after analysis include:
- locking (Evict)
- Raising an alert
D3FEND provides comprehensive, actionable knowledge to enhance cybersecurity defenses through a structured and collaborative approach.
3.3 Mapping Organizational Intel to ATT&CK
If you have a mature organization with threat analysts, start mapping tactics from previous incident reports to the MITRE ATT&CK matrix. Here’s how:
Understand ATT&CK—Familiarize yourself with the overall structure of ATT&CK:
- adversary’s technical goals
Techniques – How those goals are achieved
Procedures – Specific implementations of techniques
- Identify the behavior: Consider the enemy’s actions more broadly than merely the atomic indicator—such as an IP address—that is employed. For instance, you might observe that enemy spyware creates a SOCKS5 connection. The enemy engages in this conduct when they want to connect.
- Investigate the behavior: You might need to learn more about it if you are unfamiliar with it. A little investigation would reveal that SOCKS5 is a Layer 5 (session layer) protocol in our scenario.
- Convert the behavior into a tactic by selecting a strategy that makes sense in light of the adversary’s technical objective. In the context of the SOCKS5 connection example, creating a connection in order to communicate later would be considered a Command and Control strategy.
- Determine which strategy best fits the behavior. This can be a little challenging, but with your analytical abilities and the examples from the ATT&CK website, it’s manageable. The method Standard Non-Application Layer Protocol (T1095) appears when you search ATT&CK for SOCKS. You can see that here is where our behavior might fit in by looking at the technique description.
- Examine your findings in relation to those of other analysts. Naturally, you may interpret a behavior differently than someone else. This is typical and anticipated to occur.It is advised to discuss any discrepancies between your and another analyst’s ATT&CK mapping of the data.
Expand Intelligence Data
More sophisticated teams with the means to do so can map more external data to ATT&CK. By enlarging the data in this manner, your security teams can receive your extensive threat intelligence and use it to engage the threat defensively, resulting in a defense that is better informed about potential threats.
3.4 Detection and Analytics
Collect the Data
To build a threat-informed defense, start by collecting data from key sources:
- Process and Command Line Monitoring: Use Sysmon, Windows Event Logs, and EDR platforms.
- File and Registry Monitoring: Collected similarly via Sysmon, Windows Event Logs, and EDR platforms.
- Authentication Logs: Gather from the domain controller.
- Packet Capture: Focus on east/west traffic between hosts and network enclaves.
MITRE provides scripts on GitHub to help discover and collect this data.
Analyze the Data
After collecting the necessary data, analyze it using a search platform, typically a SIEM. MITRE’s Cyber Analytics Repository (CAR) offers guidance and contains analytics information such as:
- Hypotheses explaining each analytic
- Operational domains (host, network, process, etc.)
- References to ATT&CK Techniques and Tactics
- Pseudo code for implementation
- Unit tests to trigger the analytic
Reviewing CAR data helps analyze enterprise behaviors and expand threat intelligence by mapping behaviors to MITRE ATT&CK.
Expand and Customize Your Analysis
If you’ve started with data collection and existing analytics, expand coverage by creating custom analytics. This process familiarizes you with creating detections and analytics.
- Start with ATT&CK Techniques: Use threat intel reports linked to the techniques. For example, to detect the “Squiblydoo” variant of Regsvr32:
- Review command lines associated with Squiblydoo.
- Design a test for your analytics using these techniques.
- Test Your Analytics: Use commercial or open-source BAS solutions to test. For instance, look for regsvr32.exe creating processes and using “/i:http” in command lines, as this is indicative of Squiblydoo.
