Threat Detection with SPLUNK SIEM
As organizations grow, so does the need for proactive security measures. Splunk, as a powerful data platform, allows security professionals to detect and respond to potential threats in real time
Introduction
In today’s quickly changing cyber landscape, firms face increasingly sophisticated attacks, ranging from insider threats to external brute force attacks and port scans. Early detection and response to such threats are crucial for ensuring a safe infrastructure. Splunk, a sophisticated data platform, can assist security teams in monitoring, detecting, and responding to various security incidents in real-time by analyzing log data and finding anomalous patterns of behavior.
This blog discusses three critical use cases: suspicious file access, brute force login attempts, and excessive port access attempts, which are all intended to detect and prevent potential security issues. Using Splunk’s advanced query language (SPL), these use cases enable enterprises to implement proactive security measures and obtain insights into aberrant network activity.
In this blog, we’ll explore the following:
- Suspicious File Access: Detecting potential unauthorized access to sensitive files by users who exhibit abnormal access patterns. This can help organizations identify possible insider threats or misused privileges.
- Brute Force Login Detection: Monitoring failed login attempts that indicate a brute force attack, where attackers systematically guess passwords to gain unauthorized access to user accounts.
- Port Scanning Detection: Identifying excessive attempts to access various ports from the same source IP, which is often an indication of reconnaissance activity (port scanning) prior to an attack.
Use Case 1: Detect Suspicious File Access
Monitoring file access activities is crucial in identifying potential insider threats, misused privileges, or external attacks. Suspicious file access detection can help pinpoint unusual file activity, such as excessive access to sensitive files.
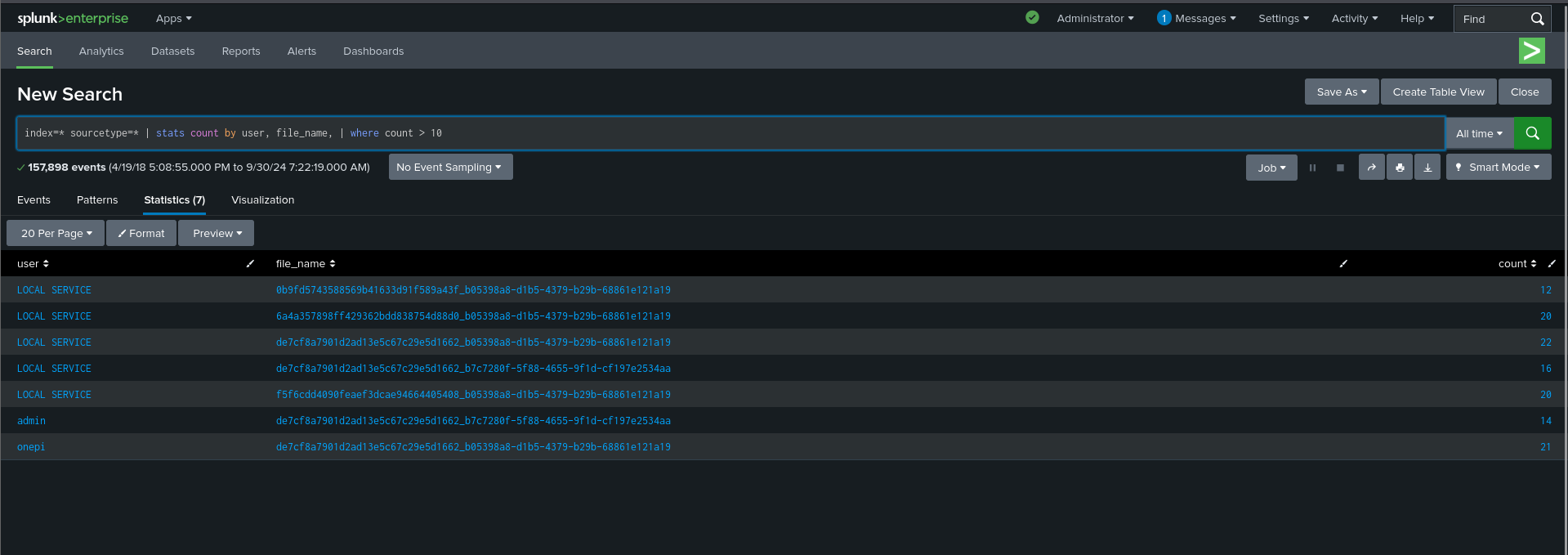
Explanation:
index=* sourcetype=*: Searches across all indexes and source types, ensuring no data source is overlooked.stats count by user, file_name: Aggregates the number of times each user accessed specific files.where count > 10: Filters the results to only show users who accessed files more than 10 times, potentially indicating suspicious behavior.
What to Look For :
- Users with unusually high access to specific files, especially sensitive ones (e.g., confidential documents or system files).
- Repeated access to critical files by non-administrative users or unexpected user accounts.
Response:
If suspicious access is detected, an immediate investigation should be conducted to determine if the user has valid reasons for accessing the files. Privileges should be reviewed and adjusted if necessary, and you may want to set up alerts for repeated access attempts.
Use Case 2: Brute Force Login Detection
Brute force attacks occur when attackers try several passwords to obtain unauthorized access to accounts. Monitoring failed login attempts enables early discovery of such operations before they succeed.
Splunk Query for Brute Force Detection:
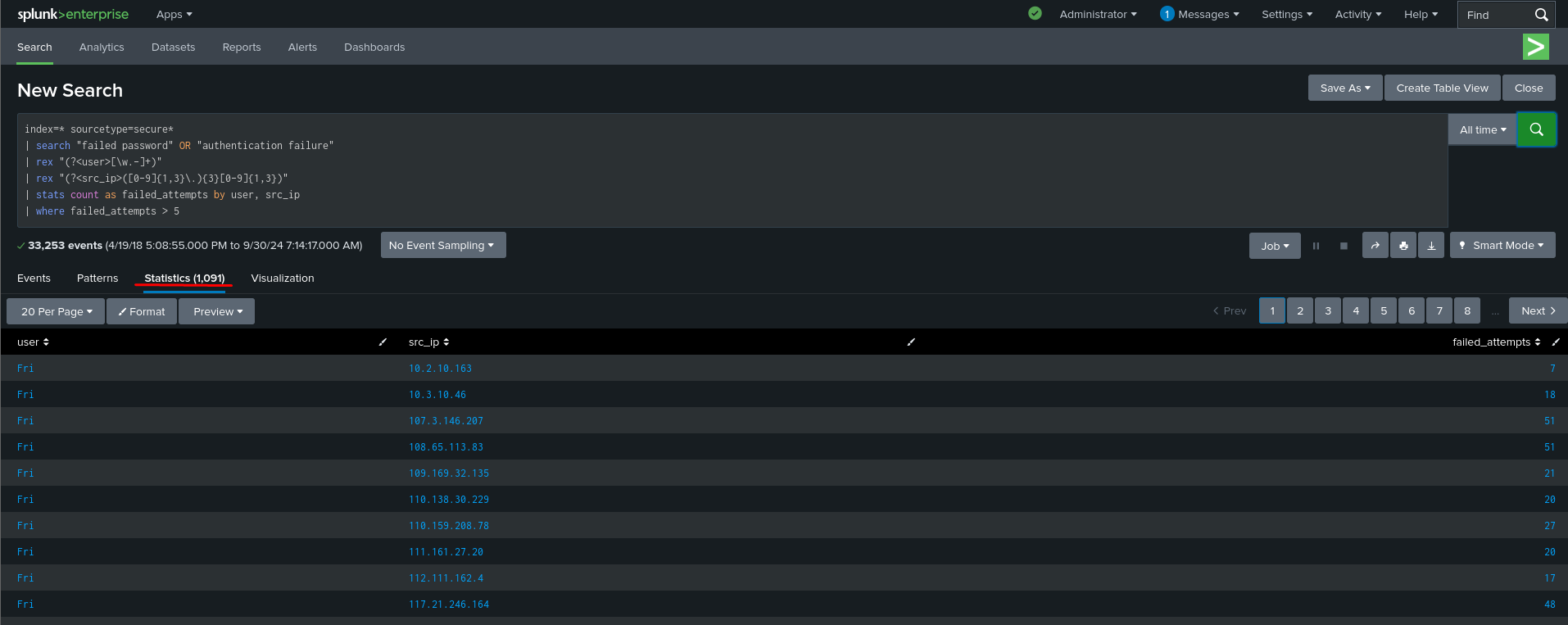
Explanation:
index=* sourcetype=secure*: Searches within secure logs, typically where authentication data resides.search "failed password" OR "authentication failure": Filters events to only show failed password attempts or authentication failures.rex "(?<user>[\w.-]+)": Extracts the username from the log data.rex "(?<src_ip>([0-9]{1,3}\.){3}[0-9]{1,3})": Extracts the source IP address attempting the login.stats count as failed_attempts by user, src_ip: Groups failed attempts by user and source IP.where failed_attempts > 5: Shows users or IPs with more than five failed login attempts, indicating possible brute force attempts.
What to Look For :
- Multiple failed login attempts from the same IP address.
- Multiple failed attempts targeting a single user account, especially privileged accounts.
- Failed logins from unusual geographic locations or unexpected source IPs.
Response:
If suspicious brute force attempts are detected, block the attacking IP address or enable multifactor authentication (MFA) to further secure user accounts. You should also investigate whether the same source IP is attacking multiple users, which could indicate a larger, coordinated attack.
Use Case 3: Excessive Port Access Attempts (Port Scanning Detection)
Port scanning is frequently the preamble to an attack, in which attackers try to locate open ports on a system in order to exploit vulnerabilities. Excessive attempts to reach different ports from the same source IP address may indicate reconnaissance efforts.
Splunk Query for Port Scanning Detection:
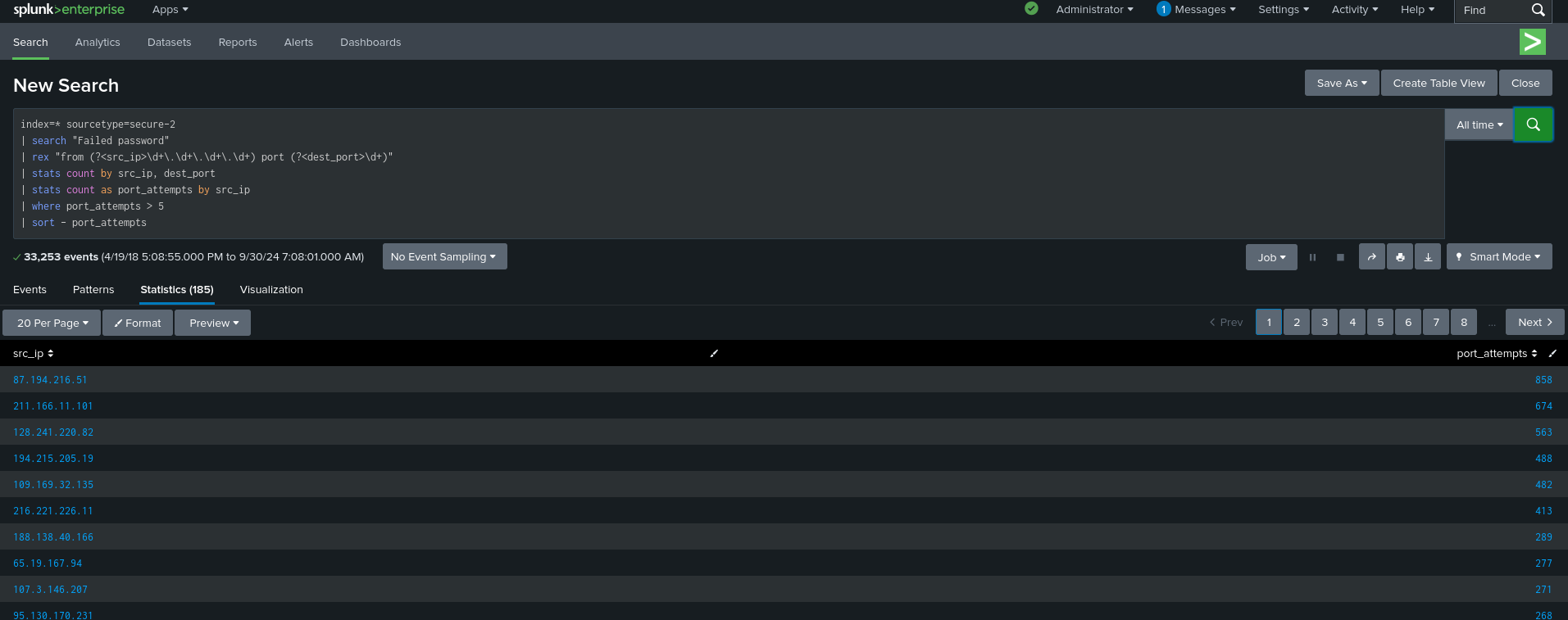
Explanation:
index=* sourcetype=secure-2: Searches within the logs that monitor secure connections and port access.rex "from (?<src_ip>\d+\.\d+\.\d+\.\d+) port (?<dest_port>\d+)": Extracts the source IP address and destination port from the logs.stats count by src_ip, dest_port: Counts the number of access attempts for each source IP and destination port.stats count as port_attempts by src_ip: Aggregates total port access attempts for each source IP.where port_attempts > 5: Filters to show IPs that attempted more than five different port accesses, which could indicate port scanning.sort - port_attempts: Sorts the results by the highest number of port attempts.
What to Look For :
- Source IPs that try to access multiple ports on the system, especially critical ports like
22(SSH),443(HTTPS), or3389(RDP). - Repeated access attempts on closed or restricted ports.
Response:
Blocking IP addresses identified as potential port scanners is the immediate action. Implementing Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can help mitigate these attempts in real-time.
Conclusion
The ability to detect suspicious behavior using suitable Splunk searches is important for current security operations. The three use cases shown in this blog (suspicious file access, brute force login attempts, and port scanning detection) provide a solid foundation for monitoring and securing your infrastructure.
Each query is intended to extract useful insights from your log data, allowing you to detect possible dangers early and respond quickly. Integrating these detections into your incident response workflows will improve your overall security posture and provide protection against both internal and external threats.
