HTB: Delivery
HTB (Hack The Box) Delivery is a beginner to intermediate-level CTF (Capture The Flag) lab focused on web exploitation, enumeration, and privilege escalation. The lab simulates a real-world environment where users must gather information, exploit vulnerabilities, and escalate privileges to gain root access.
The challenge begins with webpage enumeration and progresses to an interaction with a Mattermost chat system. Further examination may disclose user credentials that can be used to authenticate. A frequent method comprises SMTP enumeration, weak credentials, or password reuse, all of which lead to system access. Once inside, privilege escalation tactics, such as exploiting Sudo misconfigurations or misconfigured scripts, can enable you achieve root access.
Would you like a comprehensive tutorial or advice on how to solve it?
Recon
These are the following results i found through nmap scan.
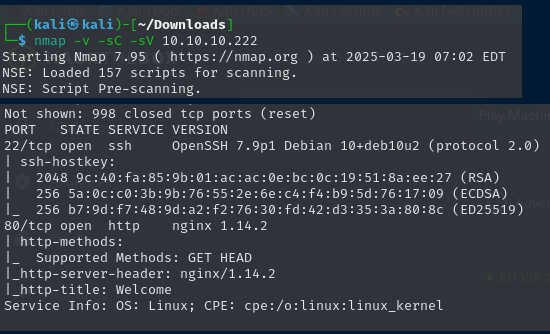
Website - TCP 80
The webpage isn’t actually for anything, but it does recommend visiting the helpdesk for email-related assistance
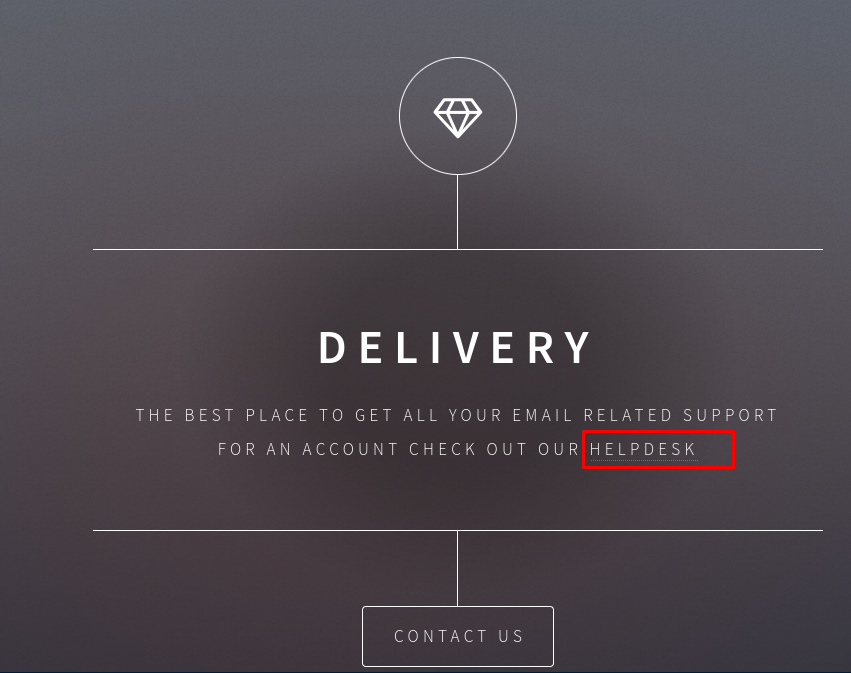
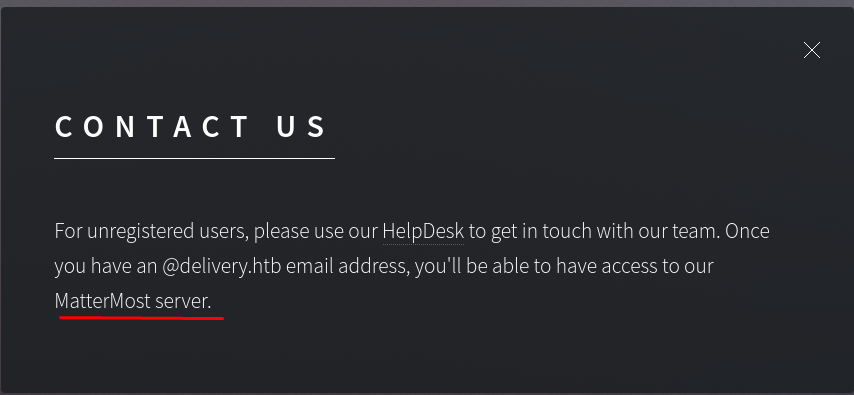
The link goes to helpdesk.delivery.htb. I’ll add both that subdomain and the base domain (delivery.htb) to my local /etc/hosts file.
The HelpDesk link is the same as the one shown above. The MatterMost server URL points to helpdesk.htb:8065, which explains the other port. There is also a hint here about the path. To gain access to the MatterMost server, I must first obtain an email address at @delivery.htb.
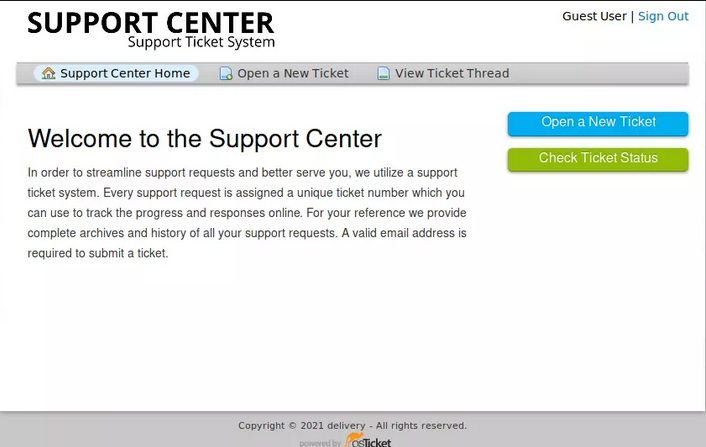
As a guest user, I can create a ticket:
And it will give me a page stating that it has been accepted.
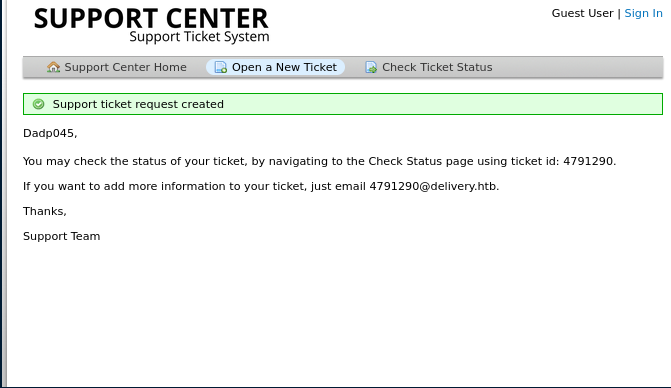
The email to add to the ticket is intriguing. I will take notice of that.
The Sign In link includes both a form and a registration link.
After choosing “Create an account” and filling out the form, I get a page that claims a link has been given to my email to activate it. On HTB, there is essentially a dead end. When I attempt to log in, it returns error.
When I click the Check Ticket Status link, I am asked to enter an email address or ticket number. Because my email address was not validated when I submitted a ticket as a Guest User, I can insert it and the ticket number:
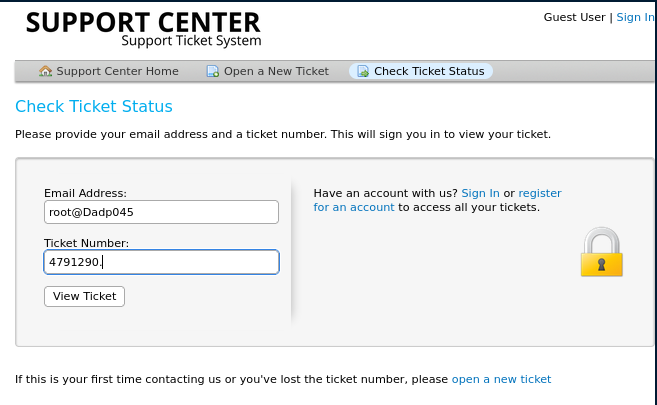
This page displays the current ticket and offers the option to amend it.
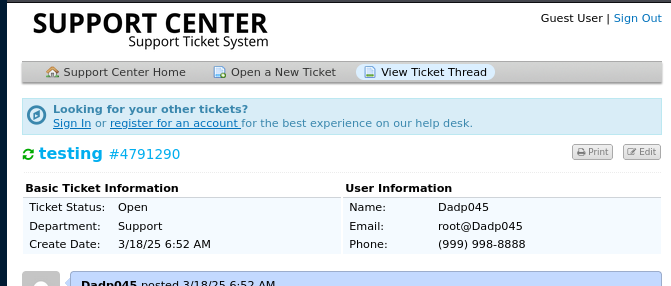
delivery.htb - TCP 8065
The create account link leads to another form.
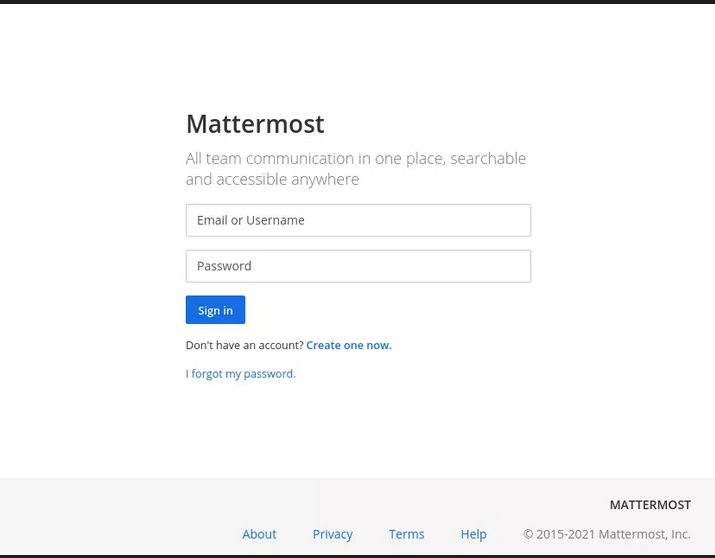
The Create Account link takes you to another form. Submitting also results in an email confirmation step.
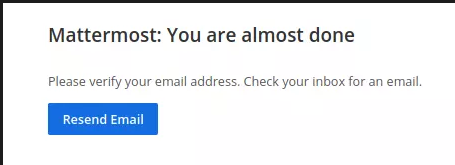
We see, without an email address, not much I can do here.
Shell as maildeliverer
Access to MatterMost
According to the note above, I needed a @delivery.htb email address to set up an account. It appears to work without one, however I can’t get emails from an outside account because HTB labs aren’t connected to the internet.
I did notice that when I created a ticket, it offered the option to edit it via email. I may use that to receive the verification email.
I will open a ticket and obtain the email address for it. Then register for a MatterMost account:
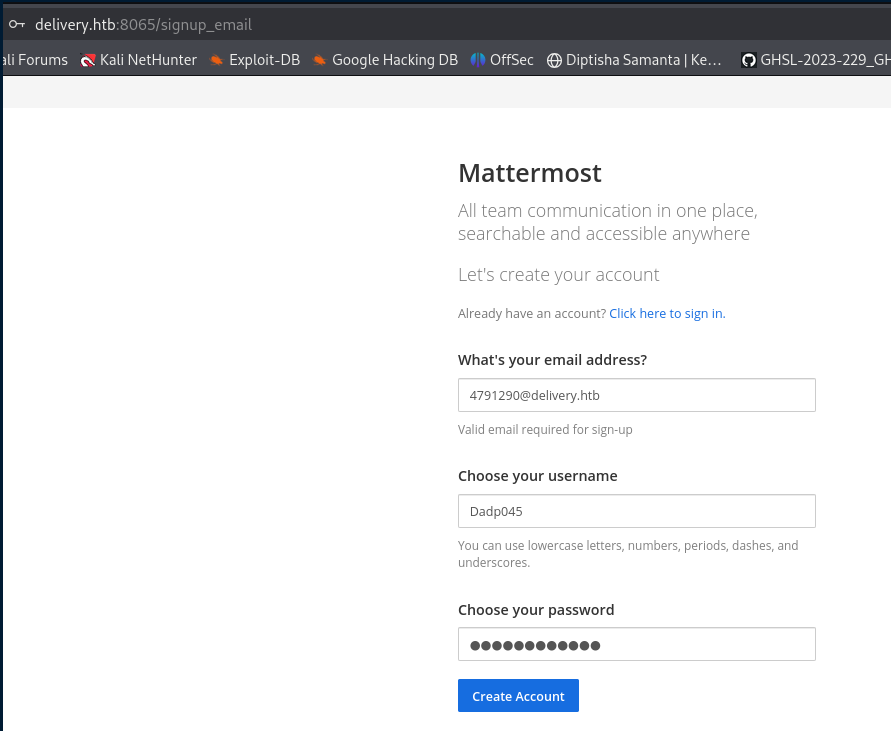
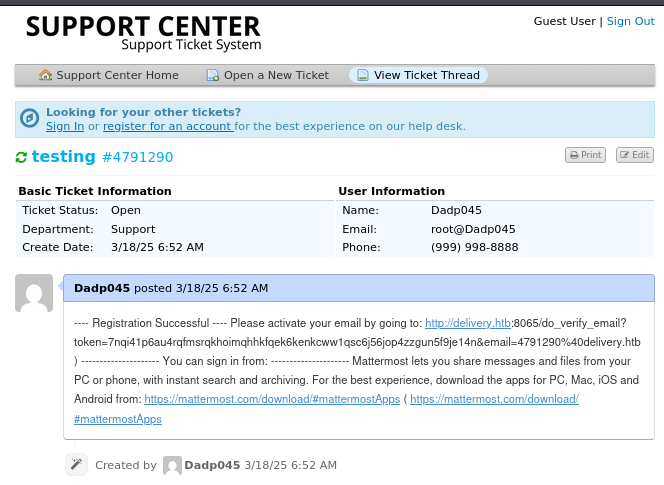
Back to HelpDesk, entering the same email address as before (root@Dadp045) and the ticket number grants access to the ticket, which contains the MatterMost confirmation email:
Once you log in, you can join a team. When you join that team, you will see a single channel with some talk from root.
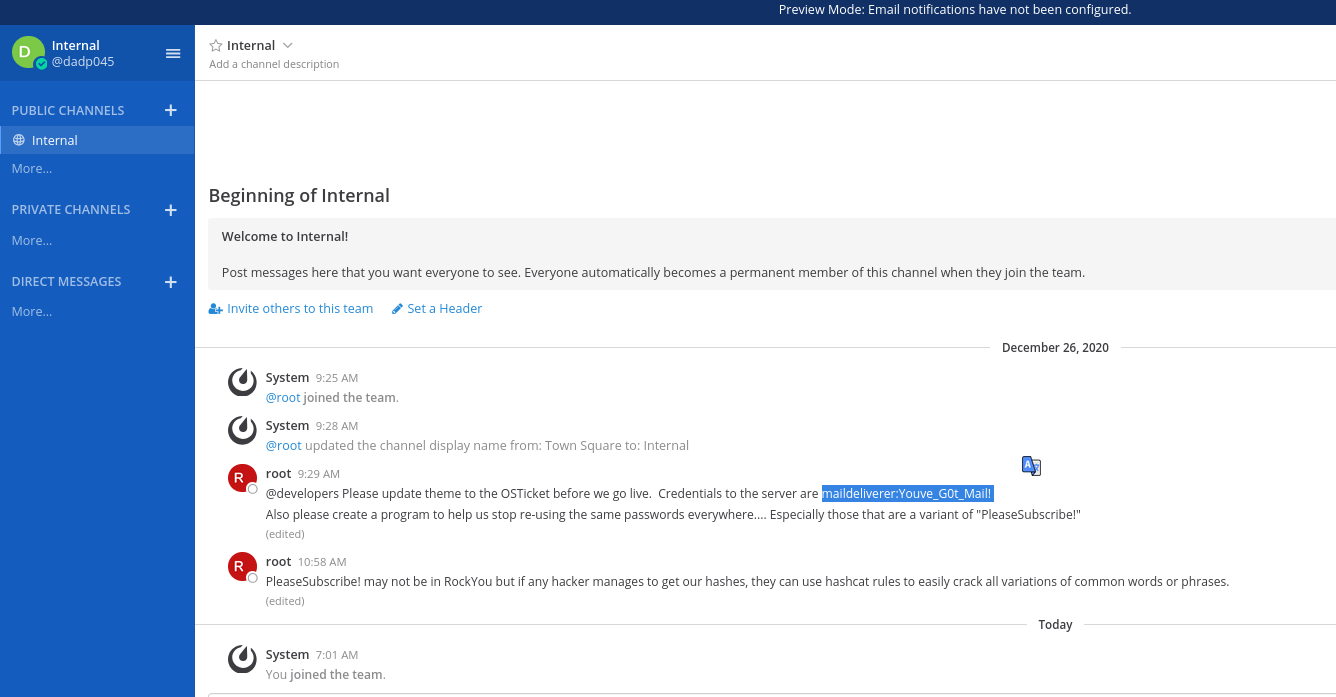
I’ll include credentials for the account maildeliverer, a hint that many of the passwords on the box are variations of “PleaseSubscribe!”, and information about how Hashcat rules will identify the variants.
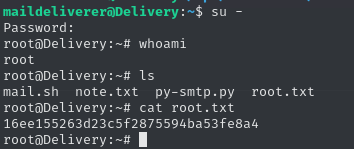
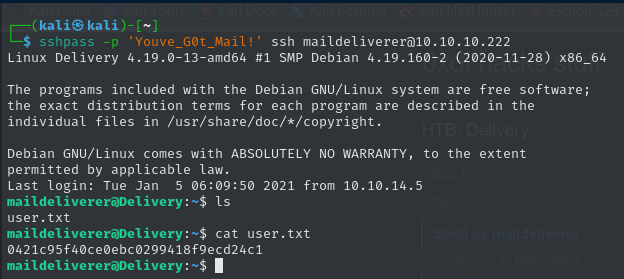
SSH
Those credentials work to SSH into the box. And get user.txt.
Shell as root
Enumeration
Mattermost’s configuration is stored at /opt/mattermost/config/config.json. The database connection information is available here:
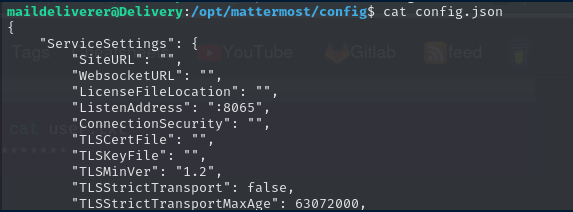

The database password is included, along with a pointer as to where to proceed next.
SQL
I’ll connect to the database using the credentials in the config above.
I see from the prompt that I’m already using the mattermost database, but if I needed to switch, using mattermost would suffice. The mattermost database contains numerous tables. I’ll start with the users’ table. Many of those look like other users or me. I will focus on the root user.
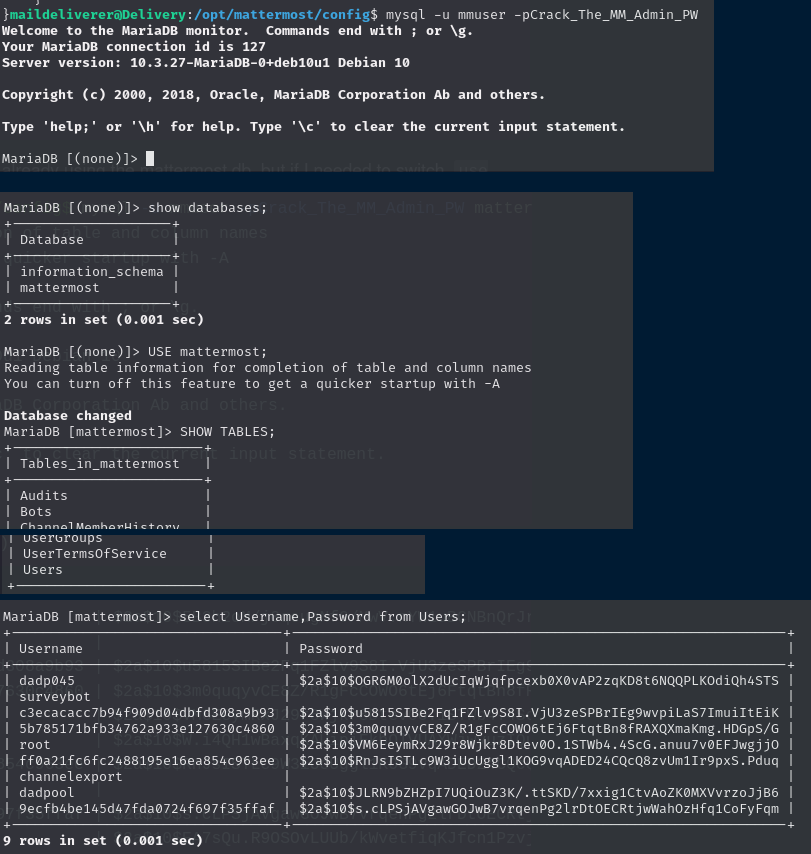
Crack Password
I’ll put the hash in a file. Based on Mattermost’s comments, I’ll generate a file with the password. Now I can use a rule file to generate multiple permutations of the passwords in the file. There are more in /usr/share/hashcat/rules, so why not start with the one titled “best”?
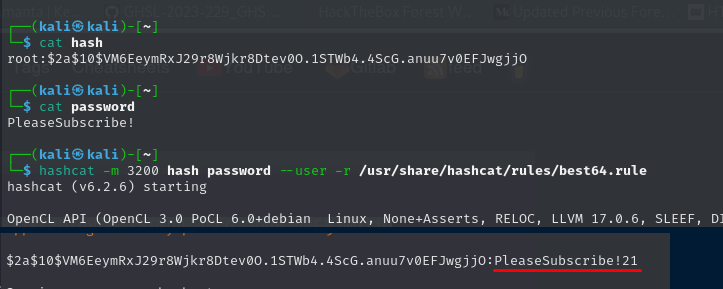
That password works for the root account in Delivery.