Monitoring Windows Logs with Splunk Universal Forwarder
The collection and analysis of logs from Windows systems is critical for monitoring security, performance, and operations. Splunk provides a simple approach to accomplish this with its Universal Forwarder, which collects and delivers Windows logs to a Splunk server for further analysis.
Introduction
In this blog, we’ll go over how to configure the Splunk Universal Forwarder on a Windows system, forward logs to a Splunk server, and use the Splunk Add-on for Microsoft Windows to properly parse and analyze logs.
What is Splunk Universal Forwarder?
The Splunk Universal Forwarder (UF) is a lightweight version of Splunk that collects logs and sends them to a central Splunk indexer or Heavy Forwarder. It is optimized for minimal resource use on the machine where it is installed, making it appropriate for production applications where performance is critical.
Key Benefits
- Efficient Data Collection: It runs in the background to gather logs, including system, application, and security logs, with minimal overhead.
- Customizable: You can configure the type and volume of data you want to forward.
- Platform Agnostic: It can be installed on both Windows and Linux systems.
What is the Splunk Add-on for Microsoft Windows?
The Splunk Add-on for Microsoft Windows is a software package that allows Splunk to interpret and parse Windows-specific logs. It includes pre-built knowledge objects (fields, tags, and event kinds) that help you search and analyze data from Windows servers, workstations, and domain controllers.
This add-on is required to extract useful information from Windows logs including event logs, performance monitoring, and security logs.
Setting Up the Universal Forwarder on Windows
Step 1:Download and Extract Necessary Packages:
- Download the Splunk Universal Forwarder from Splunk’s website. Select the appropriate version for Windows.
- Download the Splunk Add-on for Microsoft Windows from the Splunkbase.
- Extract both packages to your system (e.g., using WinRAR or another extraction tool).
- Run the installer and follow the installation steps:
- Copy the Universal Forwarder and Windows Add-on files to the Windows machine.
- Install the Universal Forwarder by running the setup file (MSI file).
- Follow the installation prompts, opting for local system setup.
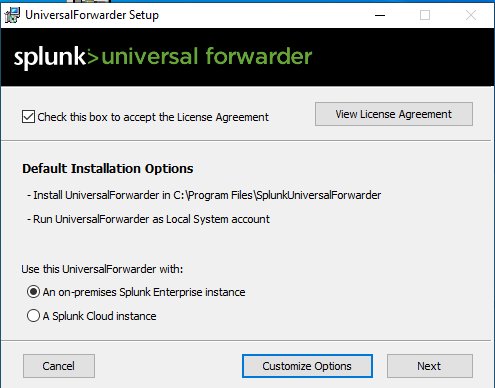
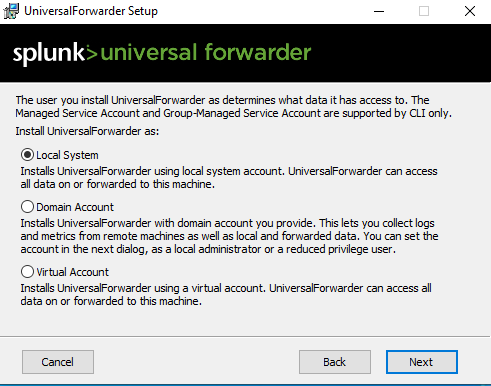
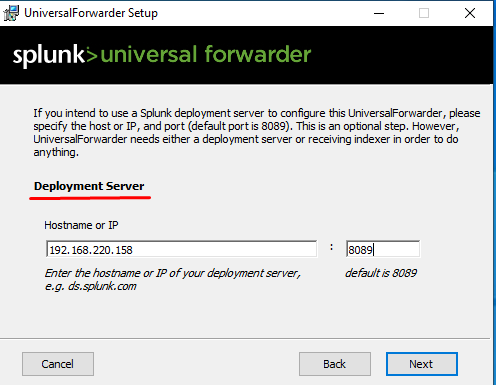
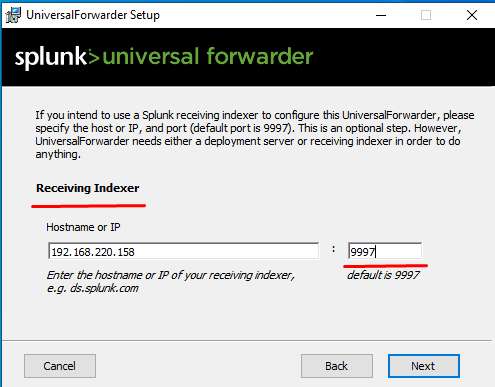
Inputting the necessary IP address of the Splunk server as the deployment server (default port 8089).Enter the IP of the Splunk indexer (on port 9997 by default).
Step 3: Install the Add-On on the Splunk Server
- Log in to the Splunk web interface on your server.
- Navigate to:
- Apps -> Manage Apps -> Install App from File.
- Upload the Splunk Add-on for Microsoft Windows file (
.tgzformat). - After installation, ensure the app is enabled.
Step 4: Configure the Windows Add-On on the Client Machine
- Copy the Windows Add-on package to your Splunk Universal Forwarder directory on the client machine:
C:\Program Files\SplunkUniversalForwarder\etc\apps\
- Create a folder named local in the directory and copy the inputs.conf file from the default directory to this new folder.
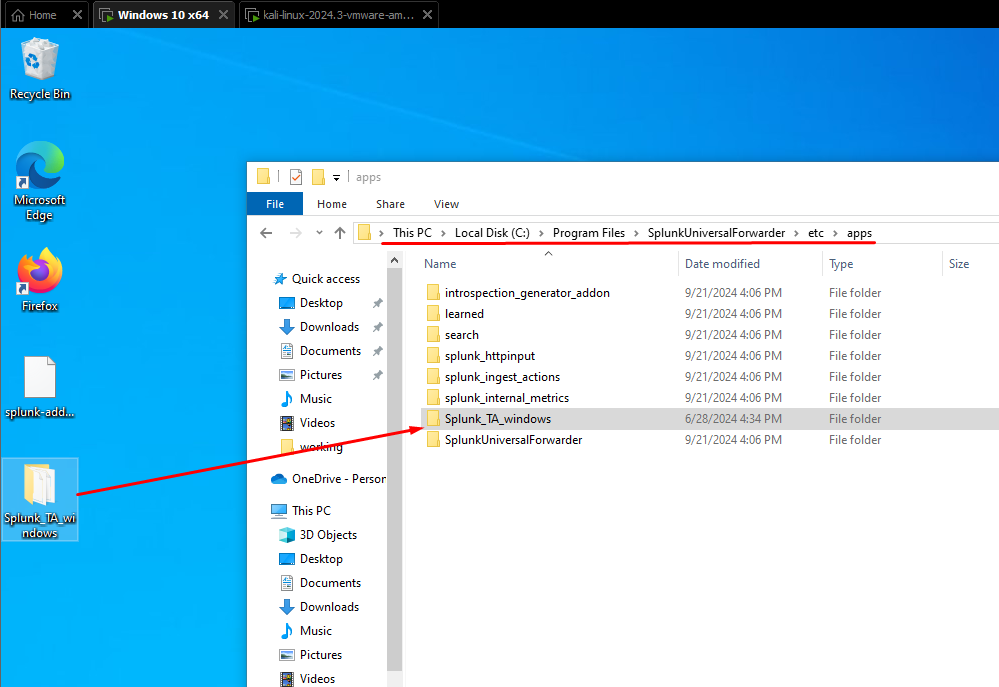
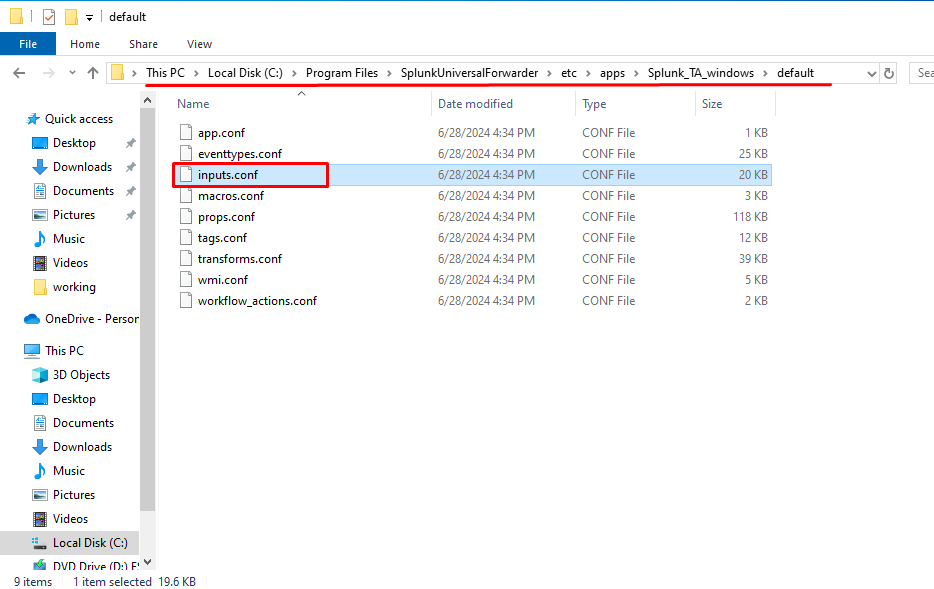
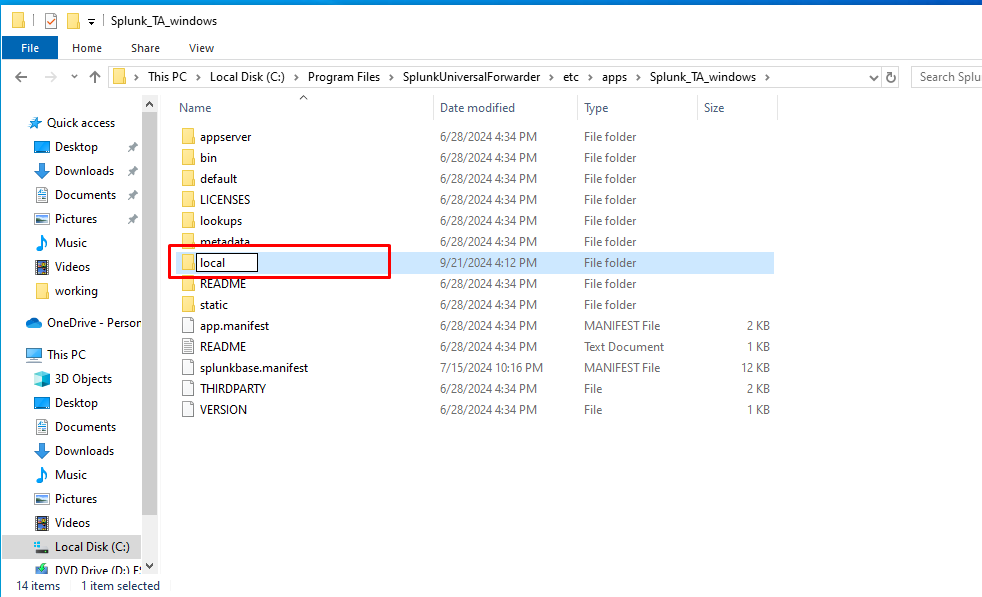
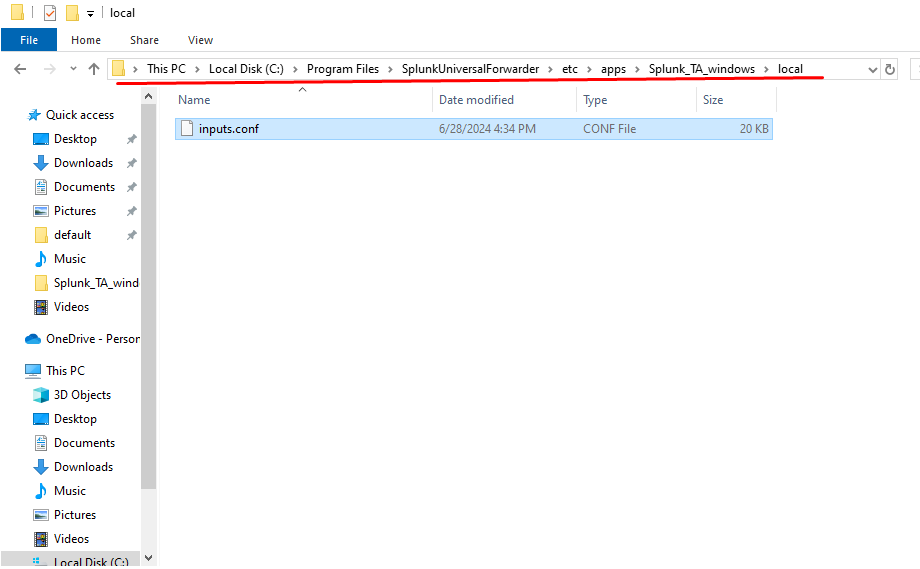
- Edit
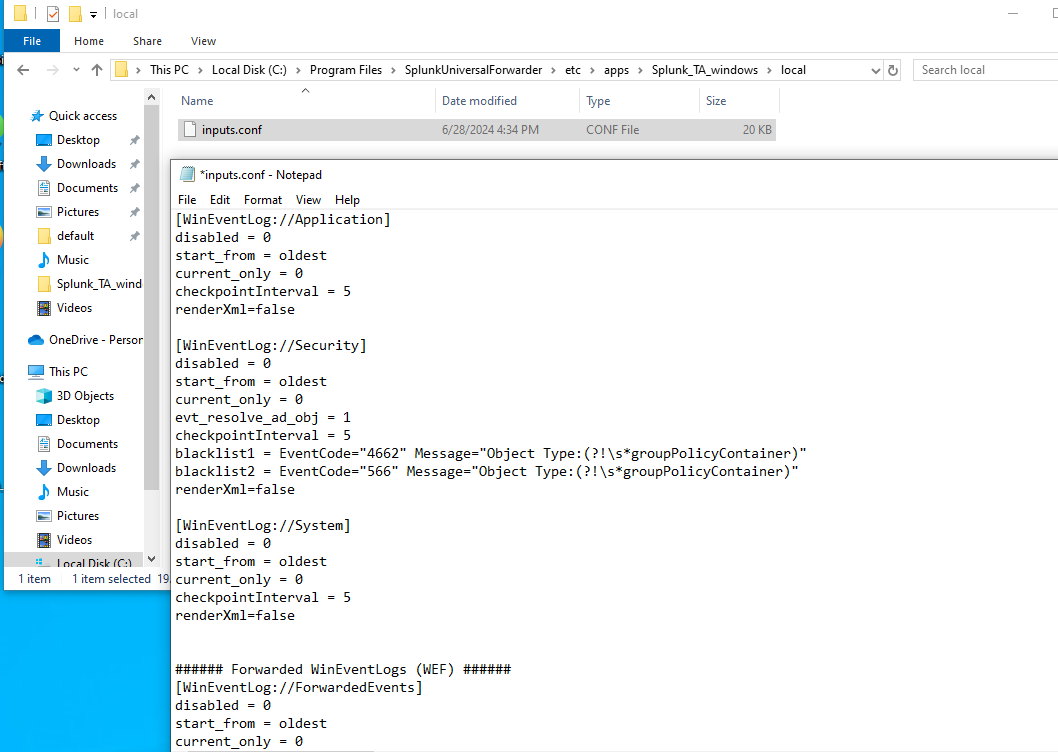
inputs.confto enable the logs you want:
[WinEventLog://Application]
disabled = 0
[WinEventLog://Security]
disabled = 0
[WinEventLog://System]
disabled = 0
Step 5: Configure Splunk Server:
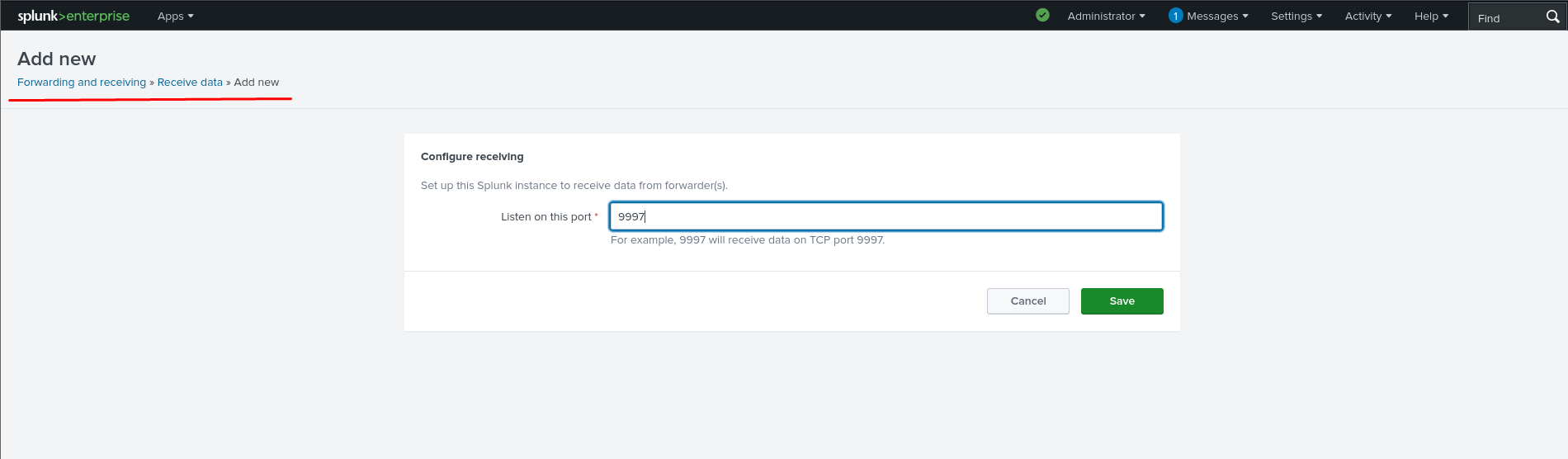
- Log into the Splunk server and go to Settings > Forwarding and Receiving > Configure Receiving.
- Add the receiving port (default: 9997) for forwarded data.
- Ensure that the Windows Add-on for Microsoft Windows is installed on the Splunk server as well.
Step 6: Restart the Splunk Universal Forwarder Service
After configuring the inputs.conf file, restart the Splunk Universal Forwarder service on your client machine:
- Open Services.msc -> Find SplunkForwarder -> Click Restart.
Step 7: Verify Data Collection
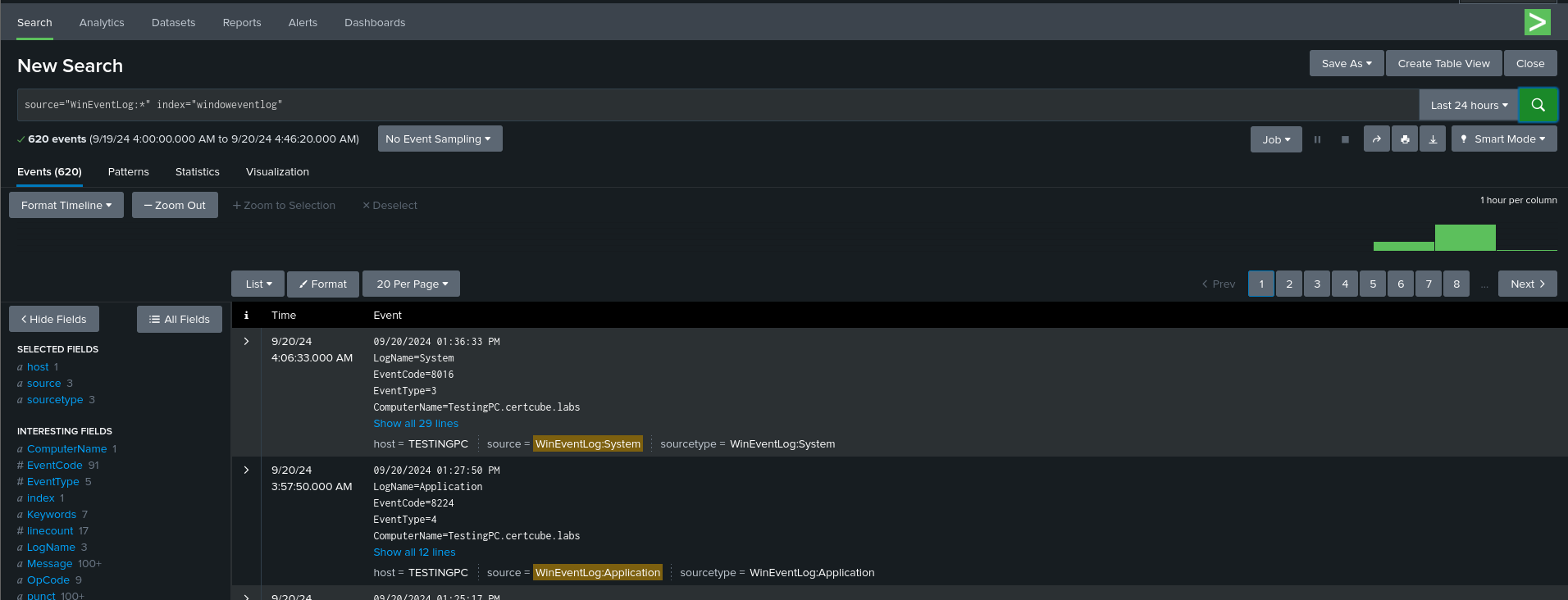
- On the Splunk server, navigate to Search & Reporting.
- Check the data summary to ensure you’re receiving logs from the Windows machine:
- host=<Windows_Client_Hostname>
- Look for events under WinEventLog://Application, Security, or System.