Foundation of Cyber Kill Chain
The Cyber Kill Chain is a security model originally developed by Lockheed Martin to describe the stages of a cyberattack. It’s widely used to help organizations understand, detect, and mitigate attacks.
Introduction
The Cyber Kill Chain Framework is an organized method for comprehending the sequential development of cyberattacks. Consider it as a path that intruders take to get into a system. It was developed in 2011 by Lockheed Martin and was based on a military theory that explains the actions an adversary takes to achieve their goals in combat, especially to eliminate or neutralize a target. The Cyber Kill Chain deconstructs an attack’s lifespan and illustrates to defenders where and how to find, interfere with, or neutralize it.
Let’s examine the elements of this framework to understand how cyber threats transform from abstract concepts to real threats and how various organizational points of intervention can be used to thwart these assaults.
Defining the Kill Chain
The military is where the concept of a “kill chain” first originated. Imagine a military operation where the goal is to neutralize a target, such as an enemy installation. They don’t just stroll over and blow it up at random. Rather, they adhere to a series of actions:
- Identify the target.
- Gather intelligence about it (How many guards? Where is it located?).
- Formulate a strategy (Should they use drones, soldiers, or artillery?).
- Attack the target.
- Assess the damage and retreat if necessary.
If something goes wrong at any point, the mission could be interrupted. Defense forces try to thwart attacks early in the chain to limit damage, which is why every military action is divided into phases.
The idea is the same in cybersecurity. To infiltrate a network or system, attackers take a number of steps. These phases are mapped out by the Cyber Kill Chain, which allows defenders to see how the attacker works and break the chain at any point. They have a better chance of stopping the attack the earlier they break the link.
The Seven Phases of the Cyber Kill Chain
The Cyber Kill Chain has seven phases that attackers typically follow. Understanding each phase helps defenders figure out how to detect and block an attack.
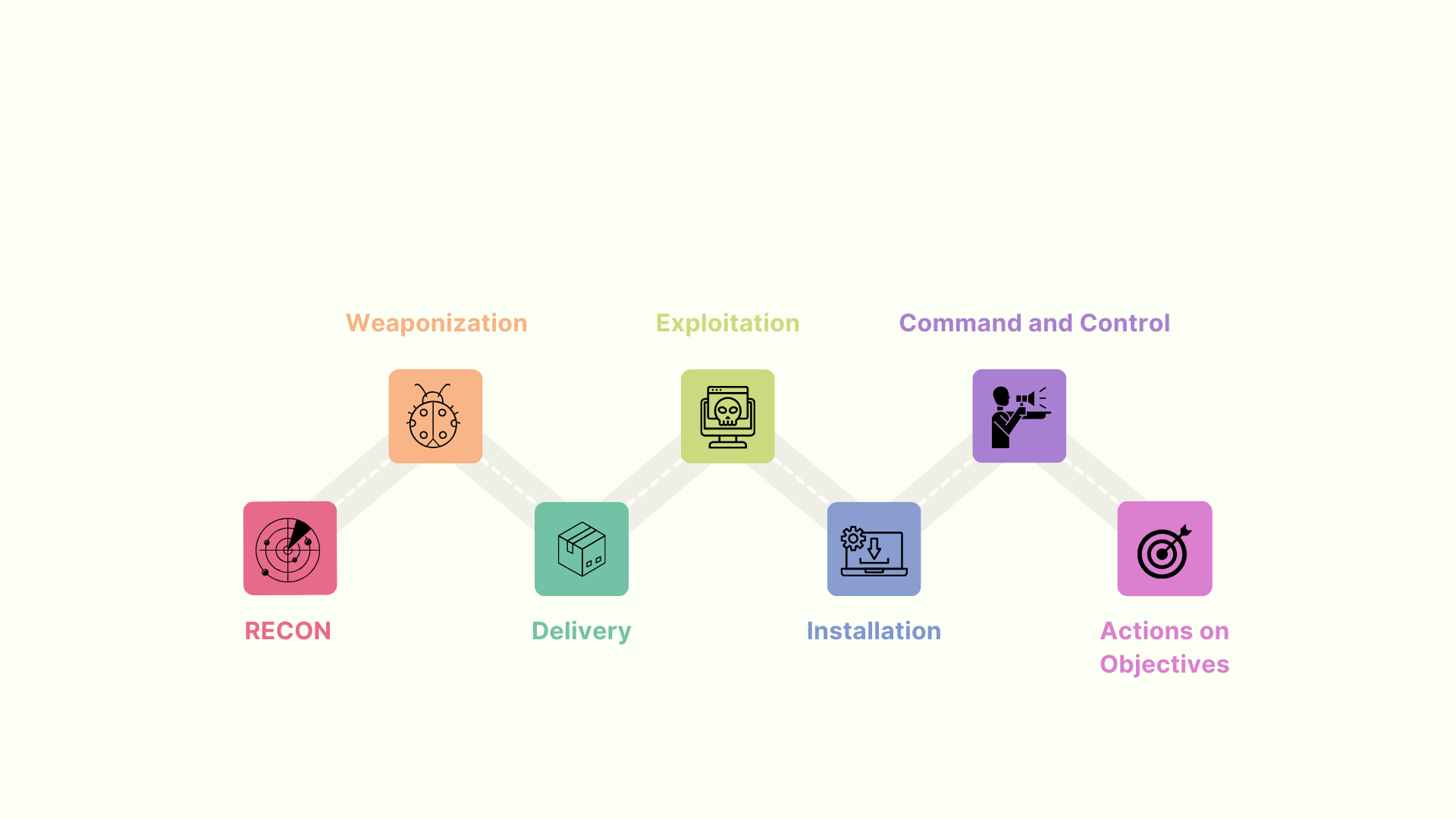
Phase 1: Reconnaissance
The first step in the Cyber Kill Chain is reconnaissance, which is essential to the attacker’s plan. During this phase, the attacker gathers information on the target through several means. This might involve anything from locating possible vulnerabilities to identifying important individuals, the network architecture, and the technologies being used. Acquiring as much information as possible before the attack is the aim.
Techniques Used:
- Open-Source Intelligence (OSINT):
Technique: Using publicly available sources to gather information.
Sub-techniques:
- Social Media Profiling: Attackers gather data from platforms like LinkedIn, Facebook, or Twitter to learn about employees or systems in use.
- Website Scraping: Gathering information from corporate websites (e.g., contact details, services offered, technology stacks).
- Public Databases: Checking public records like domain registration (WHOIS) or certificates for more details on an organization’s assets.
- Network Scanning:
Techniques: Looking for open ports and services by scanning target networks.
Sub-Techniques:
- Port scanning: To find open ports and active services, use programs like Nmap or Masscan.
- Tools that identify the software versions operating on open ports in order to identify exploitable vulnerabilities are known as service version detectors.
- Social Engineering:
Technique: Manipulating human behavior to gather information.
Sub-techniques:
- Phishing: Sending fraudulent emails to trick users into revealing sensitive information.
- Pretexting: Creating a fabricated scenario to engage with individuals to extract information.
Defensive Strategies:
- Threat Intelligence: Using threat intelligence platforms (TIPs) to obtain and examine outside data on possible assaults.
- Keeping an eye out for warning indicators use techniques (such as honeypots to identify network scans) to monitor incoming traffic for reconnaissance activities.
- Employee Education: Teaching staff members about social engineering and phishing tactics.
Phase 2: Weaponization
In this stage, the attacker creates a weaponized file or malicious code by fusing an exploit with a payload. The method that exploits a vulnerability is known as an exploit, and the malicious software that is launched when the exploit is activated is known as the payload.
Techniques Used:
- Malware Types:
- Trojan horses are malicious applications that pose as trustworthy ones.
- malware that encrypts data and demands a ransom to unlock it is known as ransomware.
- Software that tracks and steals data without the user’s awareness is known as spyware.
- Spear-Phishing Emails: These are highly targeted emails that contain weaponized attachments or links, aiming to exploit the recipient.
Defensive Strategies:
- Hardening Systems: Implementing best practices to secure systems (e.g., applying security configurations, disabling unnecessary services).
- Patching and Vulnerability Management: Continuously applying patches to known vulnerabilities to prevent exploit opportunities.
- Threat Modeling: Identifying potential attack vectors and vulnerabilities that attackers might target and applying security controls to mitigate risks.
Phase 3: Delivery
Delivery is the phase in which the attacker attempts to send the malicious payload to the victim. This could occur through email, rogue websites, compromised devices, or other means.
Common Delivery Methods:
- Phishing Emails: Emails containing malicious attachments or links to malware.
- Drive-by Downloads: Malicious websites that automatically download malware when visited
- .USB Devices: Dropped or stolen USB drives that contain malware, exploiting user curiosity.
Defensive Strategies:
- Email Filtering: Using spam filters and malware scanners to block malicious attachments or links.
- Web Filtering: Blocking access to known malicious websites or performing deep URL analysis to prevent drive-by downloads.
- Network Segmentation: Segmenting the network so that if an attacker gains access, they can’t easily move between critical areas.
Phase 4: Exploitation
Exploitation occurs when the weaponized payload is activated. This usually happens after a vulnerability is successfully exploited, allowing the attacker to run their malicious code.
Types of Exploitation:
- Software Vulnerabilities: Attackers exploit weaknesses in software (e.g., unpatched bugs, misconfigurations).
Sub-techniques:
- Buffer Overflows: Attackers send more data than a software expects, causing it to crash or behave unexpectedly, allowing the attacker to run code.
- Zero-Day Exploits: Attacks on vulnerabilities that are not yet disclosed to the vendor or the public.
- Social Engineering Exploitation: Attackers exploit human behavior to execute the payload (e.g., tricking a user into opening an infected attachment).
Defensive Strategies:
- Endpoint Protection: Using antivirus, anti-malware, and endpoint detection tools to detect and block exploitation attempts.
- Application Whitelisting: Only allowing approved applications to run, blocking any unknown or suspicious code.
- Patch Management: Keeping software up-to-date to minimize the risk of exploitation.
Phase 5: Installation
Installation occurs after the system has been exploited. The attacker now seeks to install malware or a backdoor on the compromised system, allowing them persistent access and control.
Common Malware Types:
- Rootkits: Malware that hides deep in the operating system to maintain long-term access without detection.
- Spyware: Software designed to collect information and send it to the attacker without the user’s knowledge.
- Keyloggers: Malware that records keystrokes to capture sensitive information like passwords.
Defensive Strategies:
- Malware Detection: Using tools that detect and remove malware from the system (e.g., antivirus software, anti-malware tools).
- Endpoint Detection and Response (EDR): Using EDR tools to monitor and investigate suspicious activities, and to isolate infected machines.
Phase 6: Command and Control (C2)
Command and Control (C2) is the phase in which the attacker creates a communication link between the compromised system and their own server. This connection enables them to remotely manage the infected system.
C2 Techniques:
- Domains: Attackers register domains to host C2 servers that infected machines contact.
- DNS Tunneling: A technique where attackers use the DNS protocol to transmit data between the compromised system and their server, bypassing traditional security measures.
- Encrypted Channels: Attackers often use encryption to obscure the traffic, making it harder for defenders to detect C2 communications.
Defensive Strategies:
- Network Traffic Analysis: Monitoring traffic for unusual patterns or communication with known C2 servers.
- Intrusion Detection Systems (IDS): Using IDS to detect malicious traffic patterns associated with C2 communications.
- Behavioral Analytics: Identifying suspicious behavior on infected machines that might signal the presence of C2.
Phase 7: Actions on Objectives
The attacker now has complete control of the system and can begin fulfilling their goals. These can vary based on the purpose of the attack, such as data theft, system destruction, or espionage.
Types of Objectives:
- Data Exfiltration: Stealing sensitive information, such as personal data, intellectual property, or financial records.
- Lateral Movement: Moving through the network to infect other systems and escalate privileges.
- Privilege Escalation: Gaining administrative privileges to access sensitive data or execute more damaging commands.
- Ransomware Activation: Encrypting the victim’s data and demanding payment for its release.
Defensive Strategies:
- Incident Response: Having a well-prepared incident response plan to detect, isolate, and eliminate threats as quickly as possible.
- Data Loss Prevention (DLP): Implementing DLP tools to monitor, detect, and block attempts to exfiltrate sensitive data.
- User Behavior Analytics (UBA): Monitoring user activity for unusual behaviors that could indicate compromised credentials or malicious insiders.
Conclusion: Breaking the Chain
Breaking the Cyber Kill Chain at any point is critical. Defenders should strive to disrupt the attack as soon as possible — the earlier the better. Proactive monitoring, strong defensive techniques, and incident response can help firms break the kill chain and reduce the impact of cyberattacks.
